The cyber resilience platform built into the firmware to reduce downtime
Absolute helps organizations stay operational through disruption by keeping devices controllable and access continuously trusted.
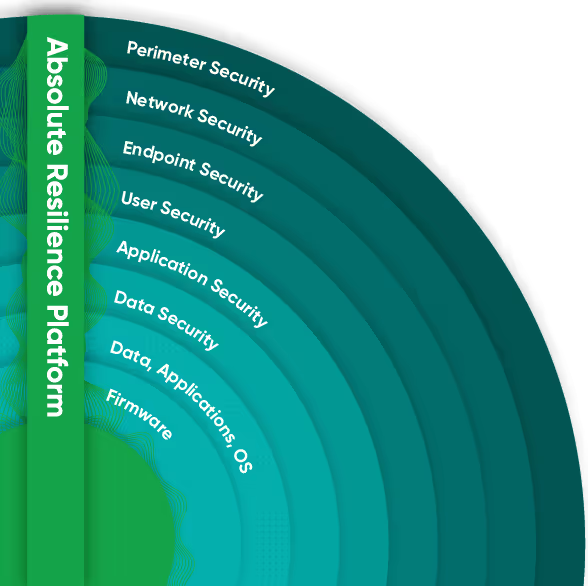
The industry's only firmware to cloud platform for resilient endpoints, servers, apps and access
Maintains device-level control during active attacks or system failures to ensure continuous manageability.
Restores compromised devices in minutes to minimize disruption and quickly return employees to productivity.
Prevents downtime by automatically restoring critical apps and security controls.
Reduces risk through automated patching and remediation across endpoints and servers.
Delivers continuous visibility and compliance confidence for security leaders.
A unified cyber resilience platform
Cyber resilience is the ability to stay operational through disruption and recover quickly when controls fail. The Absolute platform unifies Secure Endpoint and Secure Access to reduce downtime and keep businesses running. At the core of the platform is Absolute Persistence™ technology. Embedded in device firmware, it restores critical security controls, applications, and connectivity when they are disrupted or removed.

Cyber resilience delivered as a platform for endpoint and access resilience
The Absolute platform combines persistent endpoint control, resilient access, and intelligent automation to stop downtime across complex environments.


Cyber resilience platform across 600M+ enterprise devices
trusted by global enterprises across industries worldwide
active enterprise PC users secured and supported globally
mission-critical security apps supported for self-healing
OEM partners embedding resilience in firmware
Explore Absolute Security products
The Absolute cyber resilience platform unifies Secure Endpoint and Secure Access to keep organizations operational, reduce downtime, and recover faster. See the platform in action through our product tours.

Resilient endpoint control that keeps devices visible, manageable, and recoverable, even during compromise. Secure Endpoint enables rapid remediation and recovery across the distributed workforce.

Trusted, resilient access that ensures only verified users and devices can connect. Secure Access reduces risk, limits blast radius, and maintains secure connectivity across applications and environments.
Consolidated endpoint, patch and vulnerability management
Strengthening resilience across your remote endpoints.

Gain foundational visibility across your endpoints to manage your devices, applications, users and data – on or off the corporate network. Track device hardware, software, sensitive data, usage, security vitals and more and be alerted to suspicious activity and compliance drift.

Take action and respond to device or security risks. Create geofences to be alerted when devices breach approved boundaries, freeze devices when they are lost or stolen, perform a wipe or file delete to protect sensitive information, send messages to end-users and manage the supervisor password

Harden endpoints and respond to IT or security incidents to reduce downtime. Monitor app health and self-heal critical security agents, query and remediate devices at scale, investigate and recover lost or stolen devices and restore compromised devices back to a fully trusted and compliant state after an incident

Efficiently manage the deployment of patches with minimal impact on users. Proactively scan for and deploy operating system and third-party patches, prioritize devices and patches with the highest risk to keep your environment secure and schedule patch deployments in maintenance windows to reduce end-user disruption and maintain productivity

Consolidate patch and vulnerability management across your environment. Scan for and respond to operating system, software and security vulnerabilities and misconfigurations through automated remediation workflows. Build custom workflows to respond to specific exposures using a visual and intuitive workflow builder.

Boost ransomware preparedness and receive guidance from the Absolute Professional Services team to respond effectively when an incident occurs. Assess your security posture, identify and remediate the health of your endpoint management and security applications, provide tailored communication to end-users and freeze devices to limit the spread of infection.
Comprehensive SSE portfolio optimized for hybrid, mobile, and field workers
Secure, resilient access to web, cloud, and private applications.

Resilient Zero Trust Network Access with dynamic policy enforcement and Network Access Control (NAC) for always-on secure connections to public and private applications regardless of the user’s location.

Includes all the functionality in Absolute Core and adds in-line CASB, Digital Experience Monitoring (DEM) and Network Performance Diagnostics and Management (NPMD), and AI- and ML-powered proactive threat notifications for organizations that need more visibility and security.

Includes all the functionality in Absolute Edge and adds comprehensive Secure Web Gateway (SWG) capabilities including multiple AV scans, Remote Browser Isolation (RBI), Content Disarm and Reconstruction (CDR), Data Loss Prevention (DLP), and Endpoint Compliance for complete visibility and security for today’s modern workforce.
Frequently asked questions
The Absolute® Platform leverages a cloud-based, highly-available and secure multi-tenant architecture that is available across different regions. It’s comprised of a variety of foundational components that power Absolute product features that are being leveraged by the company’s enterprise customers and ecosystems partners (e.g., independent software vendors, original equipment manufacturers, or managed service providers) alike.
The Absolute Platform consists of three core components:
- Absolute Persistence Technology
Absolute Persistence® technology, a unique, patented technology is already embedded in over 600 million devices as a result of Absolute’s partnership with nearly 30 system manufacturers from around the world. Once activated, this technology is fiercely resilient and is the only solution to survive attempts to disable it, even if the device is re-imaged, the hard drive is replaced, or the firmware is updated.
No other technology can do this. Ultimately, it provides a secure, unbreakable, and always-on connection between the Absolute Platform and the endpoint, allowing you to gain unprecedented real-time visibility, control, and remediation capabilities.
- Absolute Resilience Technology
The Absolute Platform utilizes two types of patented Absolute Resilience™ technology to ensure that mission-critical applications remain healthy and operational and to provide end users with the most productive, as well as optimized remote access experience possible:
- Application Resilience™: Monitors mission-critical applications’ health and behavior; detects if missing, corrupted, or not running; and automatically repairs or re-installs components when necessary – without requiring human intervention. Application Resilience ensures security controls are working as expected and provides optimal user experience by fixing unhealthy applications. Currently more than 60 mission-critical applications are enabled for Application Resilience and more are being added frequently.
- Network Resilience™: Monitors and automatically, as well as transparently restores and optimizes unhealthy network connections so networked applications continue to operate without end user-impacting interruptions that would otherwise require manual application restarts, network re-connects, and/or re-authentications. Network Resilience allows for superior connectivity and reliability, allowing end users to focus on their tasks and not network behavior.
- Absolute Intelligence
Absolute ensures a digital tether to each device remains intact, providing you with reliable insights and intelligence from all of your endpoints to the network edge — on or off your corporate network.
Hundreds of data points are gathered and served up as insights, providing guidance on utilization, health, security and compliance posture, as well as a unified view into the entire end user experience. Applying AI-based risk assessment and user entity behavior analytics lets you go beyond the monitoring of resources and applications, allowing for automated remediation and uncompromised user productivity.
Other foundational components of the Absolute Platform that enable the Absolute Secure Endpoint™ and Secure Access™ products are as follows:
- Web console
- Mobile app
- Rules and policy engine
- Alerts
- Dashboards
- APIs
- Application Persistence-as-a-Service SDK
- Third-party integrations (e.g., SIEM, ITSM)
Customers can leverage the Absolute Platform components through Absolute’s packaged products, APIs, and SDKs. The result will be rapid innovation. The Absolute Platform is always included in the product package of choice.

