Never lose the connection when lives depend on it
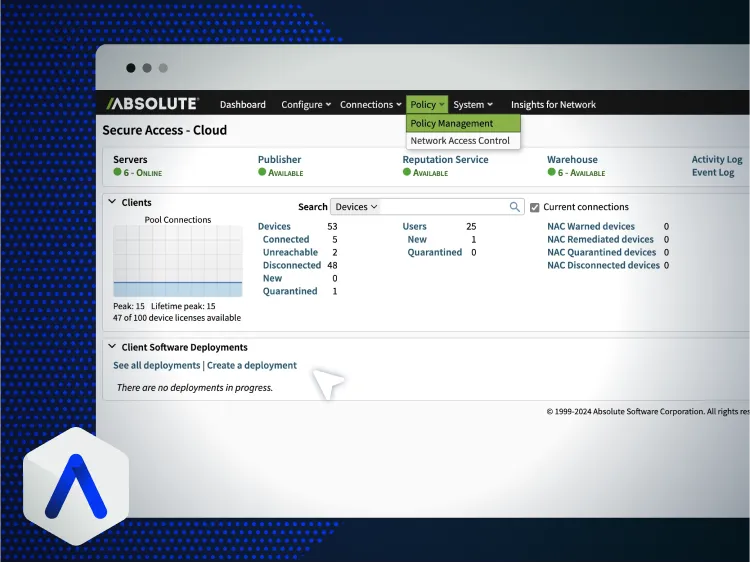


The problem
For public safety organizations, "good enough" connectivity doesn't exist. When officers are in the field, a dropped connection isn't an inconvenience; it's a breakdown in the chain of command and a risk to officer safety. It's time to stop accepting fragile access as a cost of doing business and start ensuring the resilience of your mission-critical systems.
Fragile access is a dangerous gamble
Your officers operate in a hostile environment—moving at high speed, switching networks, and working where cellular coverage is an "optimistic guess." Standard VPNs break under this pressure, leading to frozen CAD screens and failed CJIS queries. Assuming a connection will hold during a critical incident is a fundamental disconnect from reality.
Field officers should not worry about a call taking them to an area of poor coverage. Absolute Secure Access is invaluable for helping us defend against these instances. It ultimately enhances officer safety by giving them the information they need as they head into calls. Our IT staff has really noticed the support load reduction as well.
Mission continuity, guaranteed
We prioritize what keeps officers safe. With Secure Access, Mission continuity means ensuring officers remain connected to dispatch regardless of location. Ironclad CJIS compliance means secure, encrypted, and auditable connections at all times. We build a network that anticipates and survives the degradation of field operations, eliminating technology friction so officers can focus on the situation at hand.
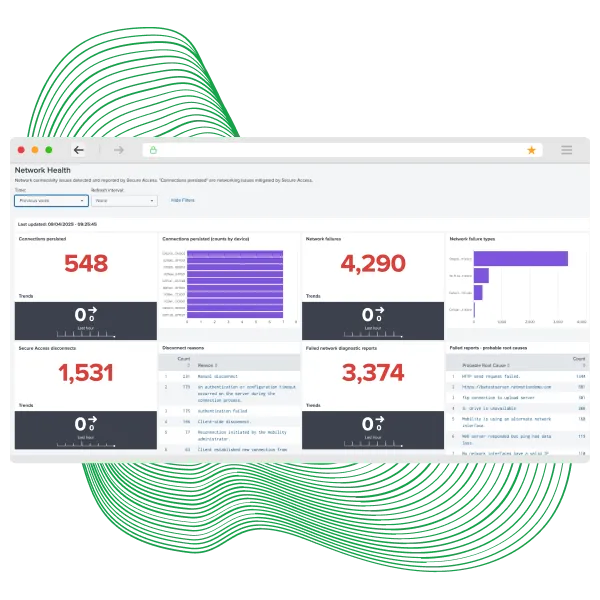
Unbreakable connectivity. Always mission-ready.
Stop accepting frozen dispatch screens. Ensure officers and first responders remain connected to dispatch and critical data systems, no matter where they are.
- Eliminate technology friction for officers in the field
- Maintain ironclad CJIS compliance without manual effort
- Ensure immediate access to criminal justice information
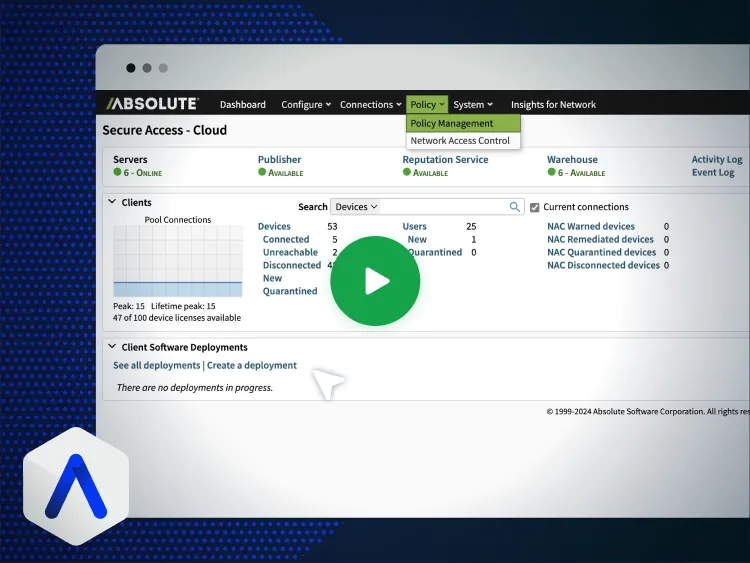


Keeping deputies safe with 100% network connectivity
Flakey VPN connectivity is a thing of the past for first responders in Coweta County. With dependable access to critical systems, deputies can respond to incidents swiftly, knowing their connection won’t let them down.
- Provides 100% connectivity across all networks, keeping responders safe while on patrol.
- Prioritizes bandwidth for critical applications via patented technology.
- Provides usage data on a single-view dashboard to quickly resolve issues.
Non-negotiable capabilities for resilient public safety
A persistent connection that pauses and resumes instantly, surviving network handoffs without session loss.
Replace brittle VPNs with per-application tunnels. Verify user identity and device posture before granting access to specific systems.
Automatically log every connection attempt and data flow to create a centralized, audit-ready trail for CJIS mandates.
Enforce least-privilege access based on real-time factors like device health, location, and user role.
Protect the mission with Secure Access
The operational reality of policing has changed. Standard corporate IT solutions like legacy VPNs were never built for this hostile environment. Our guide reveals how a unified foundation provides persistent visibility and control from the device to the data center, turning a chaotic environment into a manageable, secure ecosystem.
Inside you'll learn:
- Why legacy VPNs fail during critical incidents
- How to achieve Zero Trust in the field without friction
- Automating CJIS audit readiness
- Reducing technology friction for officers
.webp)
Ensure 100% connection with Secure Access
When your team is in the field, their focus should be on the mission, not the technology. Let's discuss how you can build a truly resilient connectivity strategy that keeps your officers safe, compliant, and always connected.
- Officer Safety: Eliminate distractions caused by connectivity troubleshooting.
- Operational Resilience: Build a network that survives field degradation.
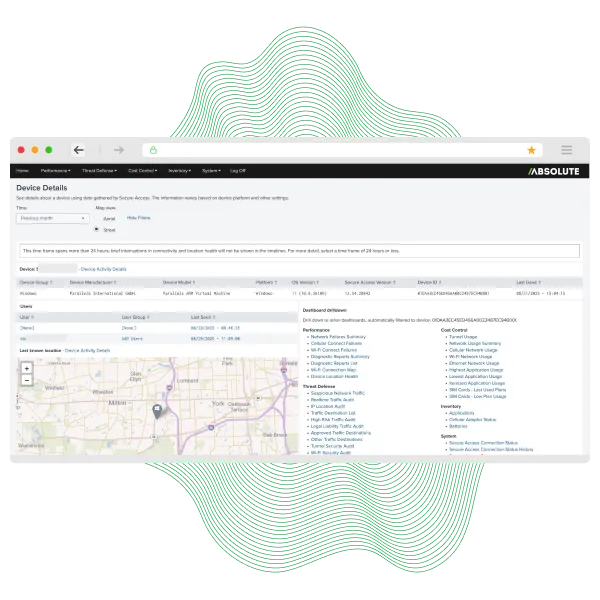
Essential reading for public safety professionals
FAQ Answers for public safety IT and security leaders
Standard VPNs are session-based and brittle. They panic when the network switches from Wi-Fi to LTE, or when packet loss occurs, killing the session and forcing a login restart. Our solution uses a persistent tunnel that survives these changes invisibly.
Proving compliance is often a manual nightmare. We provide a centralized audit trail that automatically logs every connection attempt, policy decision, and data flow, turning a stressful audit into a simple reporting task.
It complements them. Mobile routers provide the physical link, but they often introduce complications. Our software optimizes that link, managing the traffic flow and persistence to ensure the application layer remains stable even if the router struggles.
Traditional VPNs give broad network access, which is a security risk. Zero Trust grants access only to specific applications based on identity and context. This reduces the attack surface while simplifying the login experience for the officer.
Yes. The same resilient technology applies to tablets, handhelds, and laptops used outside the vehicle, ensuring a consistent, secure experience for detectives and foot patrol officers on untrusted networks.
