From Hatch to Dispatch—Secure, Compliant, Unstoppable
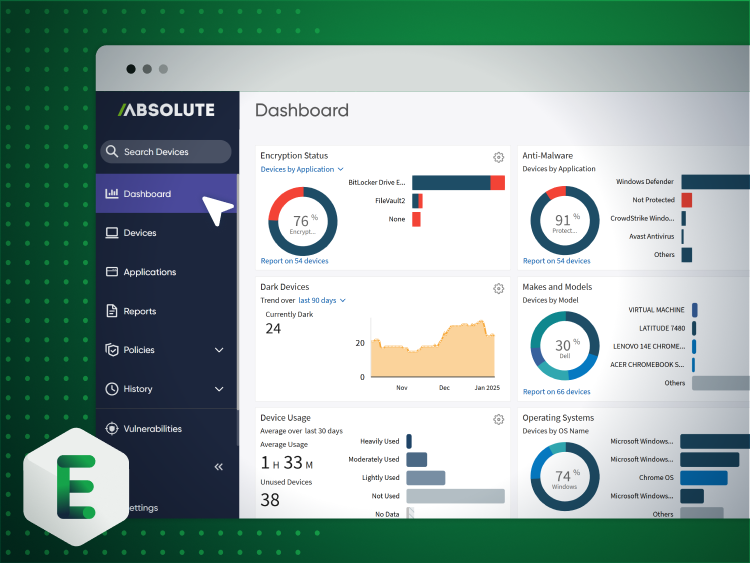


The problem
Device lifecycle management isn’t just messy; it’s controlled chaos with a security price tag. We hand out laptops and then… what? Outdated tools leave us guessing, and every offboarded employee could mean a ticking time bomb of cached credentials. Why accept blind spots, data exposure, and compliance risk as the cost of doing business when you can lock down every stage: from hatch to dispatch, with complete control?
A cascade of risk and lost value
Every lost device is a potential breach. Every un-wiped machine is a financial liability. Every missing patch, unmanaged configuration, or untracked device creates a cascading risk—data loss, breach exposure, operational disruptions, compliance failures, and financial waste. Can’t keep endpoints in line? You’re handing bad actors the keys and writing off assets early.
Apart from the fact that we now have an additional level of computer security and an effective way to recover lost and stolen hardware, I can communicate to the rest of the organization and others that we have a solution like Absolute Secure Endpoint which acts as a deterrent against future theft.
Lifecycle control that never lets go
Forget fragile agents and fleeting visibility. Absolute’s firmware-embedded connection delivers an unbreakable tether to every device, everywhere: so control is guaranteed, not guessed. From remote provisioning without disruption to freezing, tracking, and wiping endpoints when employees leave, you maintain full command across the entire device life cycle. Secure NIST-compliant data wipes ensure peace of mind, while auditable reports keep finance and compliance teams satisfied.
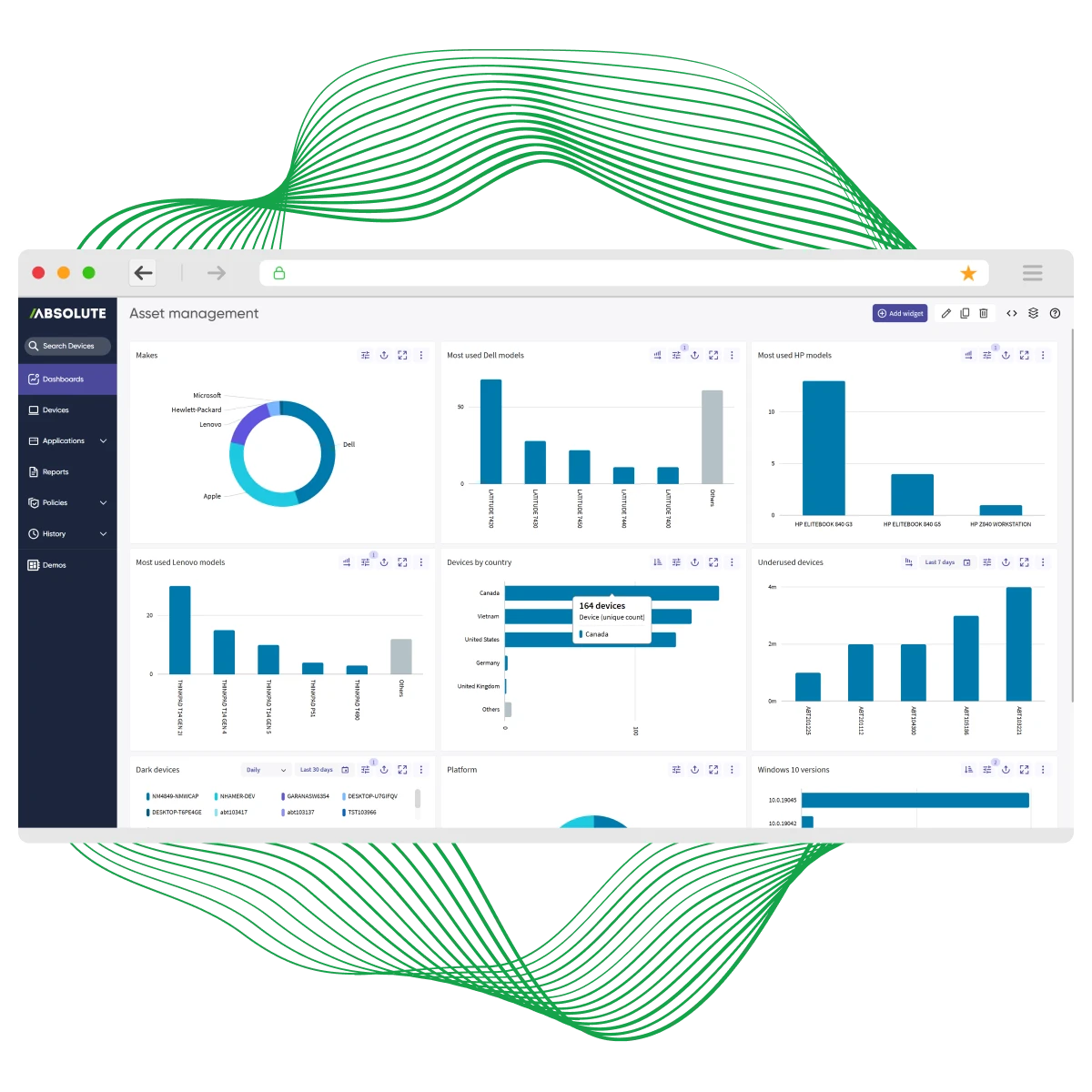
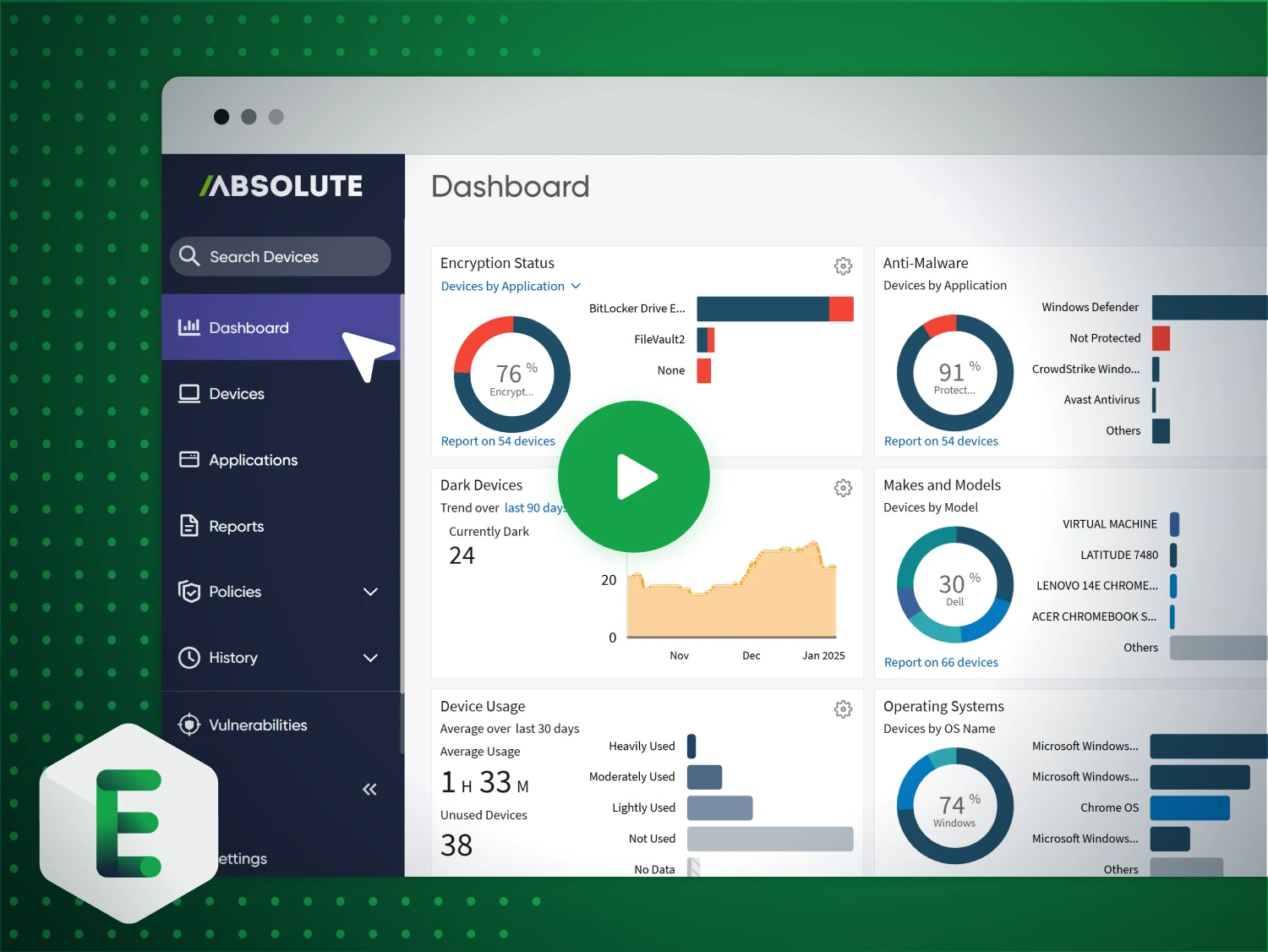
See device lifecycle management in action
Stop managing endpoints by chance. Take the tour and discover relentless, lifecycle-wide control, automated patching, secure recovery, and proof at every stage
- Prove Endpoint Resilience: See how firmware-embedded technology keeps devices connected and secure; even off-network.
- Automate Compliance & Recovery: Explore workflows for patching, NIST-compliant data wipes, and auditable reporting that simplify IT and security operations.


Assala energy: securing devices across remote operations
Operating in challenging environments, Assala Energy needed guaranteed visibility and control over every endpoint. With Absolute, they achieved resilient connectivity and lifecycle-wide security—even in the most remote locations.
- Unbreakable Device Connection: Maintain visibility and enforce security policies across distributed assets, no matter the network conditions.
- Streamlined Compliance: Automate NIST-compliant data wipes and generate auditable reports for regulatory peace of mind.
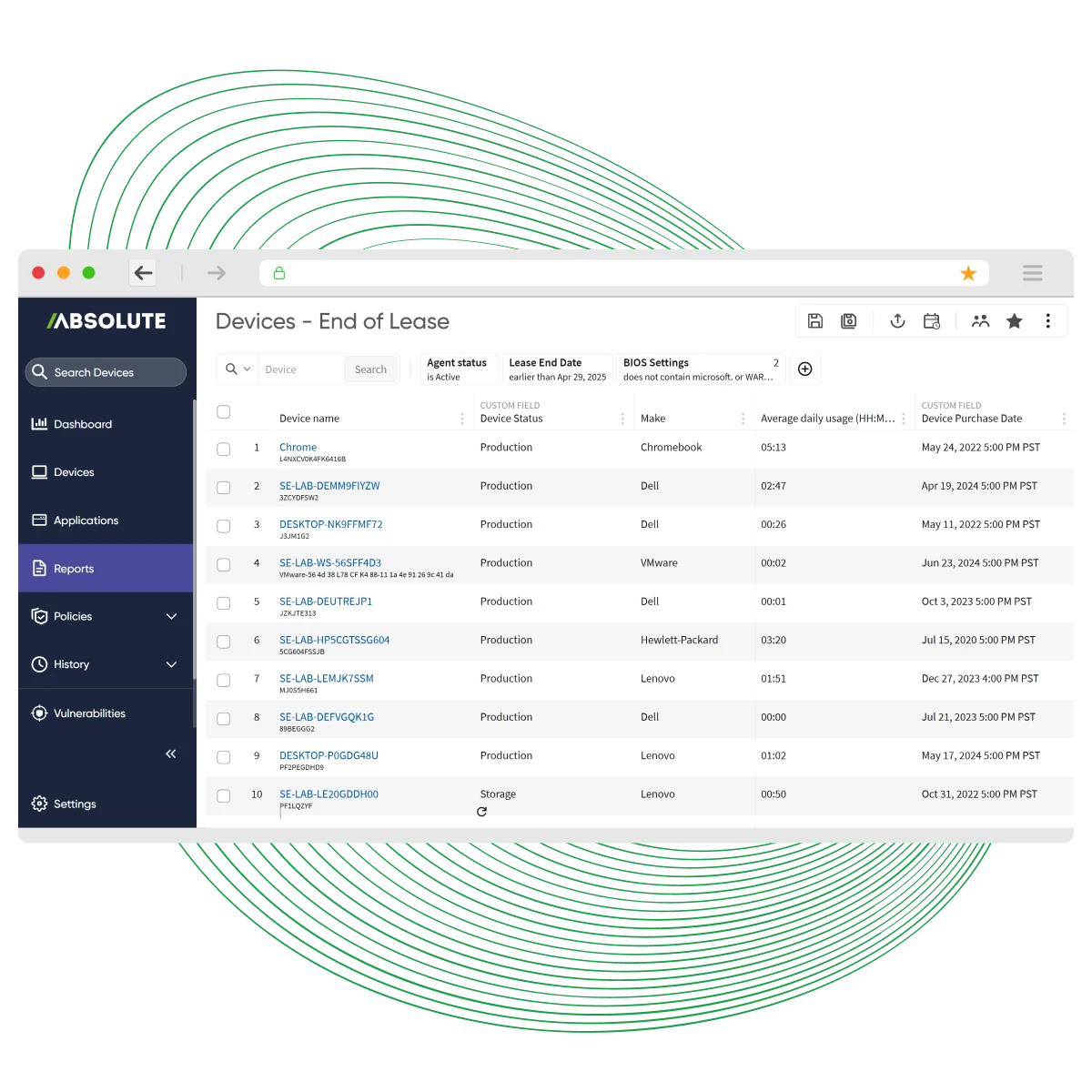
Key capabilities for device lifecycle management
- Zero-touch provisioning
- Asset inventory and discovery
- Recycle devices with confidence
- Configuration baselines & drift remediation
- Persistent endpoint control
- Automated OS and application patching
- Application deployment & updates
- Kiosk & shared device modes
- Physical device recovery
- Secure decommissioning & data wipe
- Prevent unauthorized post-termination access
- Financial write-offs & charitable donations
Build resilience across the entire device lifecycle
Learn how Absolute’s firmware-embedded persistence transforms lifecycle management—delivering visibility, security, and compliance from deployment to decommission.
- Control Every Stage: From remote provisioning to secure NIST-compliant data wipes, see how persistence ensures uninterrupted management throughout the device lifecycle.
- Simplify Compliance & Reporting: Gain auditable proof of security posture and automated remediation—reducing risk and operational overhead.

Request a trial
Stop guessing—start experiencing full visibility and control. Get hands-on with Secure Endpoint and see how effortless IT asset management can be.
- Set up devices automatically with zero-touch provisioning
- Automate OS and application patching without a VPN
- Execute NIST-aligned data wipes for secure decommissioning
- Define POV goals to suit your organization
Featured resources for Device Lifecycle Management
Device lifecycle management FAQ
Unlike standard tools that rely on removable agents or on-premises connections, Absolute embeds a permanent, undeletable link in device firmware for true, self-healing control—no matter where the endpoint is.
Absolute executes wipes aligned with NIST 800-88r1 standards and provides a digitally signed certificate of sanitization, offering auditable proof for compliance, tax write-offs, or secure donations.
Cached credentials on decommissioned devices are instantly revoked remotely—online or offline—closing a common gap that often leaves corporate systems at risk after separation.
Automated patching, provisioning, and reclamation turn lost devices back into inventory, cut manual labor, and provide proof for finance, audits, tax write-offs, and risk mitigation.
Automation reduces manual tasks like onboarding, patching, and remediation, allowing teams to focus on exceptions instead of repetitive work—boosting efficiency, not workload.
