Stop serving the tools. Start serving the mission.


The problem
Running government IT is a high-wire act. You’re balancing immense scale against rigid oversight, managing thousands of endpoints across state agencies and federal departments. But legacy tools fracture at this scale. When an agent is disabled or a VPN drops, you're left with a security blind spot. It's time to ask: are you upholding the public trust, or just fighting fires?
Complexity is a threat to the mission
We've accepted that compliance is a frantic, manual scramble. We assume that when a device leaves the network, it’s a black box. This is a dangerous fallacy. In a landscape of strict NIST and FISMA mandates, relying on "point-in-time" security or spreadsheet inventories isn't just inefficient—it's negligence.
Deployment was painless and I’ve been impressed by the exceptional customer service I’ve received. Our account manager went above and beyond in making sure we had products set up appropriately and installed correctly so we could use the functions we needed.
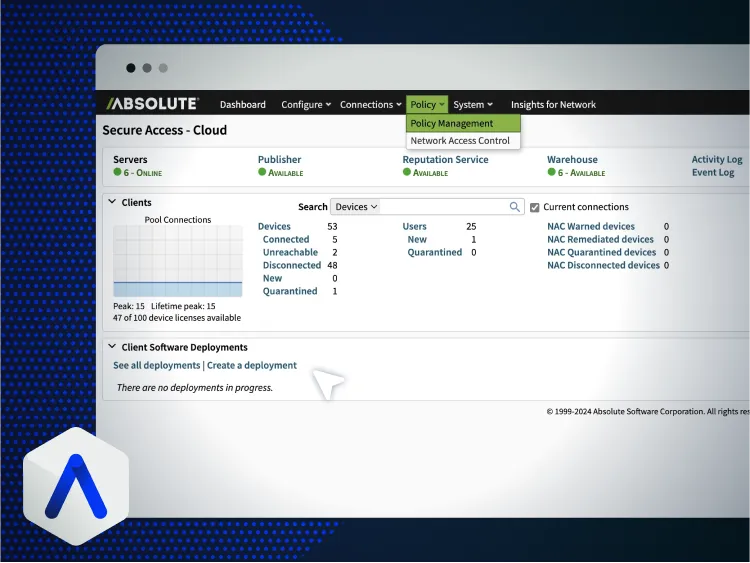
Unquestionable compliance, total control
Secure Access is your cornerstone for safeguarded connectivity and Zero Trust control, even for the most distributed and demanding public sector environments. Resilience for Automation shifts compliance from frantic checks and fire drills to real-time, fully automated policy enforcement. These solutions work together to deliver unquestionable compliance through continuous evidence collection, drive total asset accountability with live inventories that leave no device unseen, and unlock operational resilience so critical public services stay online, effective, and secure; no matter what gets thrown your way.
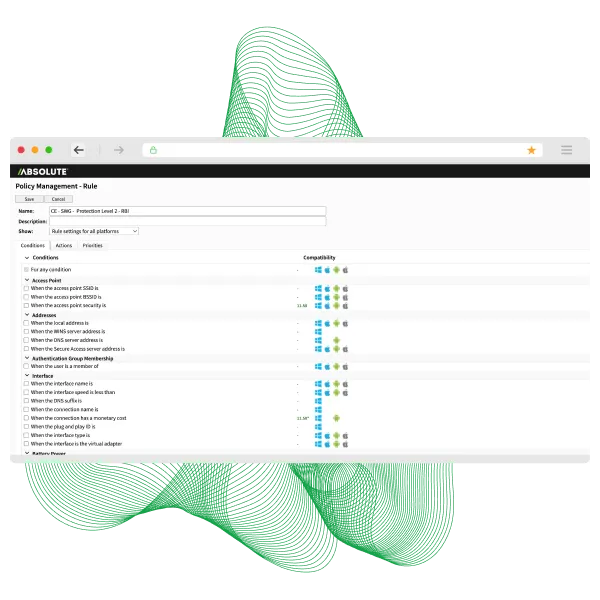
Secure connectivity for a distributed workforce
Government work has left the building. Field agents and remote caseworkers need reliable access, but legacy VPNs expose the entire network to risk. The Secure Access ZTNA model that grants secure, direct access on a per-application basis. This ensures remote workers get exactly what they need, while the rest of the network remains invisible.
- Resilient Connectivity: Maintain persistent sessions that survive network drops, keeping field teams productive.
- Least-Privilege Access: Drastically reduce attack surface by eliminating broad network access.


Resilience in action: U.S. Environmental Protection Agency
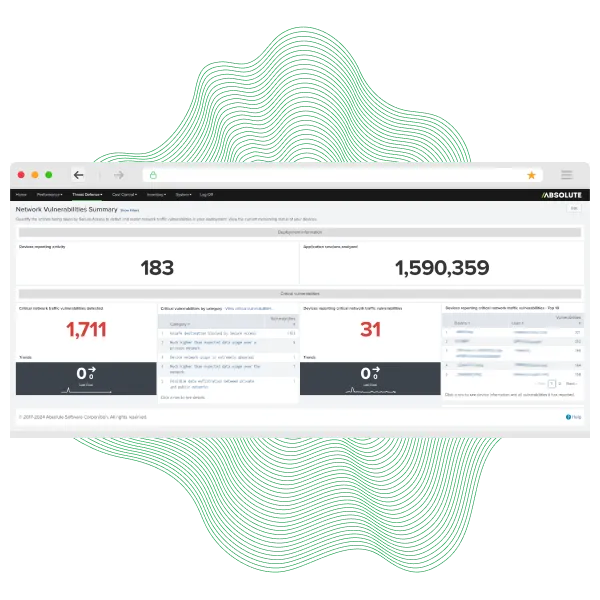
The U.S. EPA secures and manages over 20,000 endpoints nationwide by using Secure Endpoint for real-time visibility and control. With security embedded at the firmware level, the EPA gained continuous compliance, faster threat response, and accurate asset tracking with minimal manual effort.
- Firmware-Level Visibility: Continuous asset tracking, on and off the network
- Automated Compliance: Effortless evidence collection for audits and reporting
- Rapid Incident Response: Remotely locate, lock, or wipe endpoints as needed
Essential capabilities for government resilience
Create an unbreakable tether to every device for live inventory of all hardware and software, regardless of location.
Continuously monitor and enforce policies to generate audit-ready reports on demand for NIST and FISMA.
Ensure critical controls (encryption, AV) are always running by automatically repairing them if tampered with.
Grant granular access to specific apps, ensuring field workers stay connected without exposing the network.
Enforce least-privilege access based on real-time factors like device health, location, and user role.
A persistent connection that pauses and resumes instantly, surviving network handoffs without session loss.
Replace brittle VPNs with per-application tunnels. Verify user identity and device posture before granting access to specific systems.
Master mission readiness
The unique pressures of government IT require more than just managing devices; they demand mastering mission readiness. Our guide explores how a unified platform dissolves silos, combining unbreakable endpoint connection with resilient access. Stop managing tools and start managing risk.
Inside you'll learn:
- Strategies for continuous, automated compliance
- How to eliminate "black box" devices from your inventory
- The ROI of reducing the attack surface proactively
- Building operational resilience for public services

Build a foundation of trust with Secure Access
Ready to finally break away from unreliable VPNs and complexity? See how Secure Access enables resilient, compliant connectivity for your remote teams and field staff—no more gaps, no more guesswork. Boost operational readiness and never lose sight of your assets or your mission.
- Seamless Connectivity: Keep every user linked to the mission.
- Compliance by Default: Make audits a non-event.
Essential reading for government IT and security professionals
FAQ Your resilient government IT questions answered
Audits are usually a manual drain on resources. We automate the collection of evidence and policy enforcement. This means you can generate audit-ready reports on demand, proving compliance instantly rather than scrambling for weeks.
Yes. Our technology is embedded in the firmware, creating a persistent connection to the device regardless of the operating system status or network connection. If it has power and an internet connection, you can see it and manage it.
Traditional VPNs offer "all or nothing" access. Our ZTNA approach is granular. A field worker gets a resilient tunnel only to the specific case management app they need. If their device is compromised, the attacker can't move laterally across the agency network.
Absolutely. We understand the patchwork nature of government IT. Our platform provides a unified view and control plane that works across modern laptops and legacy workstations alike, ensuring no asset is left behind.
Yes, our endpoint security solutions have achieved FedRAMP authorization, ensuring they meet the rigorous security standards required for federal deployment.
