Mastering Zero-Trust Technology in 2025
Cybersecurity vulnerabilities are in a constant state of flux. For security leaders, the mission is clear: protect digital assets, mitigate risk, and maintain operational resilience. Zero trust is no longer a niche concept but a foundational strategic imperative for achieving these goals. It provides a robust framework for minimizing attack surfaces and enabling risk-based access policies. However, separating an effective strategy from marketing noise remains a significant challenge.
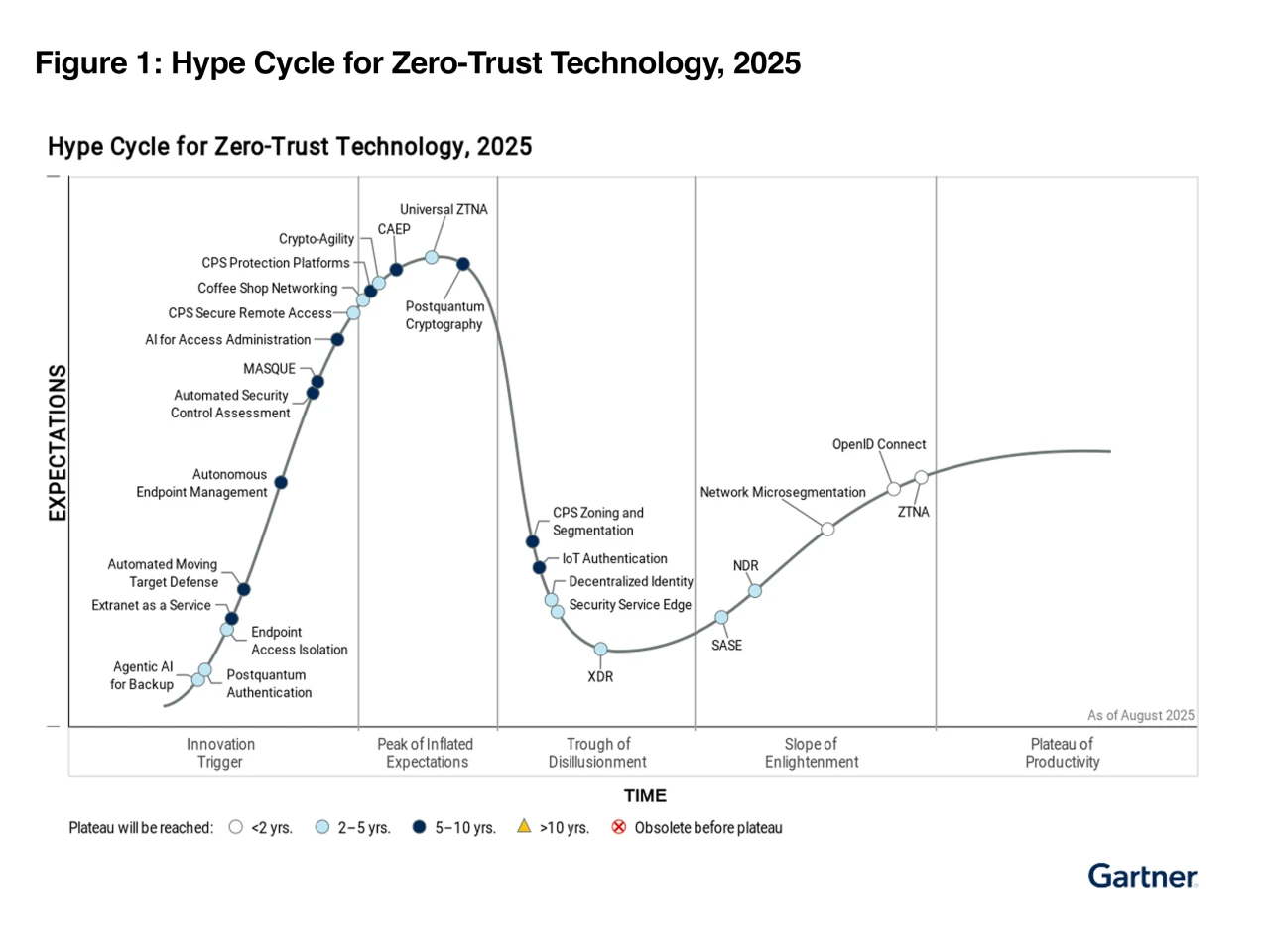
As organizations navigate complex, distributed environments, a mature zero-trust approach is essential. This requires more than just implementing a single technology; it demands a comprehensive strategy guided by the latest industry insights. In our view, the 2025 Gartner® Hype Cycle™ for Zero-Trust Technology offers a definitive roadmap, providing the clarity needed to prioritize technology investments and build a security posture that is both resilient and future-ready.
The Evolution of Zero-Trust Strategy
Zero trust is a framework, not a product. Successful adoption depends on the careful selection and integration of technologies across its core pillars: positive identification, explicit policy enforcement, adaptive access, and continuous monitoring.
The next wave of zero-trust innovation is here; the focus is shifting toward a more dynamic, intelligent, and proactive security model. This evolution is critical for safeguarding an expanding array of devices and distributed data across hybrid environments, from traditional IT to the operational technology (OT) and Internet of Things (IoT) ecosystems.
Key Drivers of Zero-Trust Adoption:
- AI for Adaptive Security: AI enhances threat detection, dynamic access controls, and endpoint management with speed and accuracy.
- Automation: Simplifies modern security, reduces manual work, and ensures faster, consistent threat responses.
- Post-Quantum Preparedness: With quantum computing on the rise, investing in post-quantum security and advanced authentication is crucial for a future-proof zero-trust strategy.
Why We Think the Gartner® Hype Cycle™ Report Is Essential
Navigating the crowded marketplace of zero-trust solutions requires strategic guidance. In our view, this report delivers the insights that could help you build and refine your security roadmap. It offers a clear view of which technologies are poised to deliver transformational value, and which are still in their nascent stages.
This complimentary Gartner® report will equip you to:
- Prioritize technology innovations that are most effective for advancing your organization’s zero-trust security posture.
- Distinguish genuine best practices from marketing hype to ensure your investments deliver real-world value.
- Expand zero-trust principles beyond traditional IT to protect the full scope of your digital and physical assets.
- Develop a strategic approach to postquantum security to proactively address emerging, sophisticated threats.
Build a Resilient, Future-Ready Security Posture
An effective zero-trust architecture requires a unified effort across cybersecurity and infrastructure teams, backed by strategic investments in people, processes, and technology. This report serves as an invaluable tool for fostering that collaboration and justifying the necessary resource allocation.
Stay ahead of the curve and fortify your organization’s defenses against the threats of today and tomorrow. Gain the strategic advantage you need to lead your organization with confidence in an era of ever-present cyber risk.
Download your complimentary copy of the 2025 Gartner® Hype Cycle™ for Zero-Trust Technology today to strengthen your security strategy.
Gartner, Hype Cycle for Zero-Trust Technology, 2025, Tiffany Taylor, Andrew Lerner, 1 August 2025.
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally, and HYPE CYCLE is a registered trademark of Gartner, Inc. and/or its affiliates and are used herein with permission. All rights reserved.
Gartner does not endorse any vendor, product or service depicted in its research publications and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s Research & Advisory organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.








