Streamlining IT and security operations in a complex threat landscape
Endpoints now span home offices, shared workspaces, and global networks — each a potential entry point for ransomware, data breaches, or compliance failures. Meanwhile, IT and security teams are tasked with managing an ever-growing stack of tools, integrations, and workflows that often don’t communicate seamlessly with one another.
When those systems become fragmented, visibility suffers and response times slow — exactly the conditions that cybercriminals exploit. Streamlining IT and security operations has never been more critical to building cyber resilience.
At Absolute Security, we believe resilience begins with simplicity. By unifying endpoint visibility, control, and self-healing capabilities within a single platform, organizations can close operational gaps, enforce consistent policies, and respond to threats faster — before they escalate into costly incidents.
That’s the driving force behind the Absolute Secure Endpoint 10.1 release: delivering focused enhancements that make managing and securing endpoints more integrated, automated, and effortless for the teams who depend on them.
What’s new in version 10.1
The 10.1 release introduces practical enhancements that help IT and security teams consolidate workflows, automate safer processes, and accelerate response across their environments.
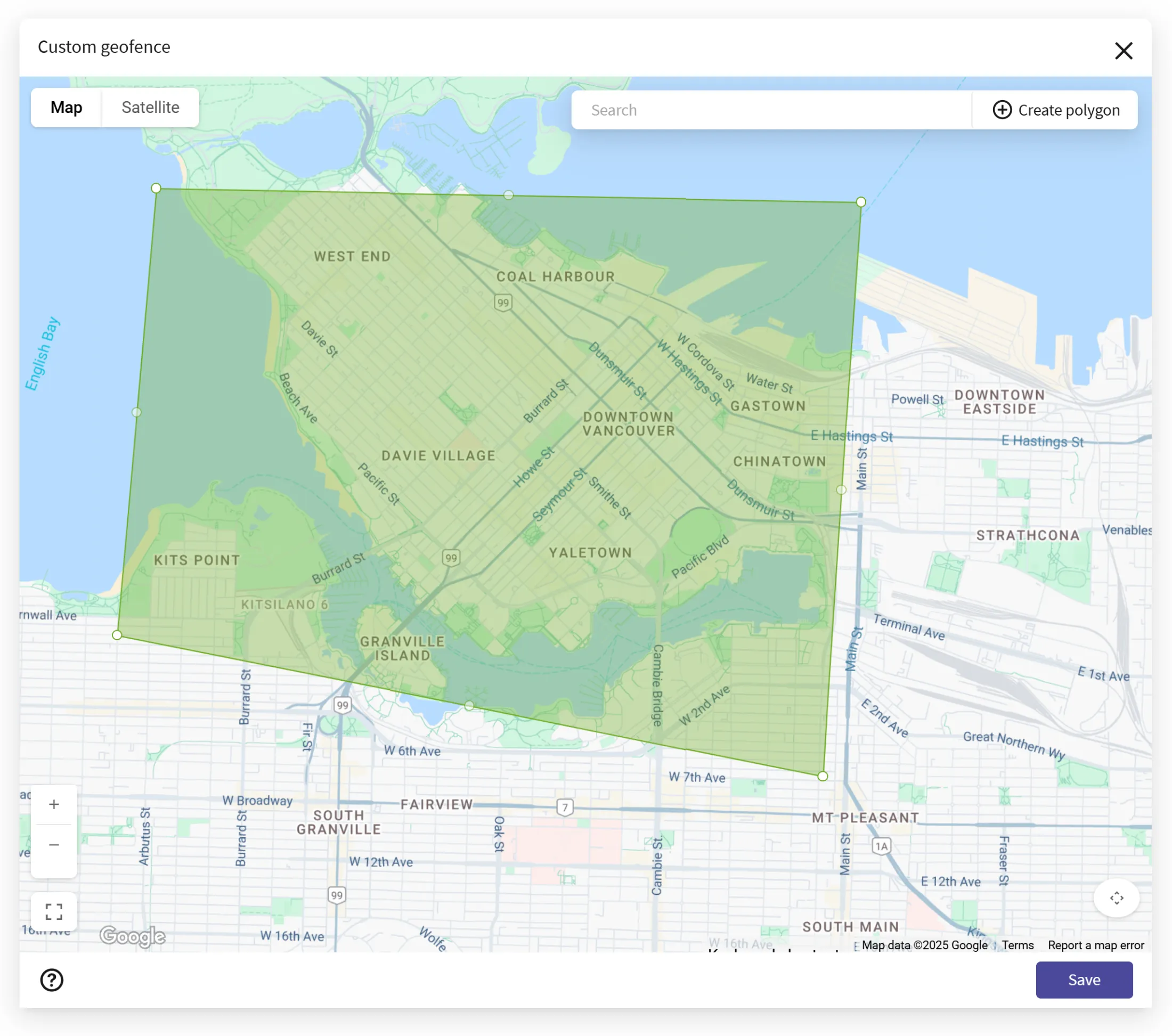
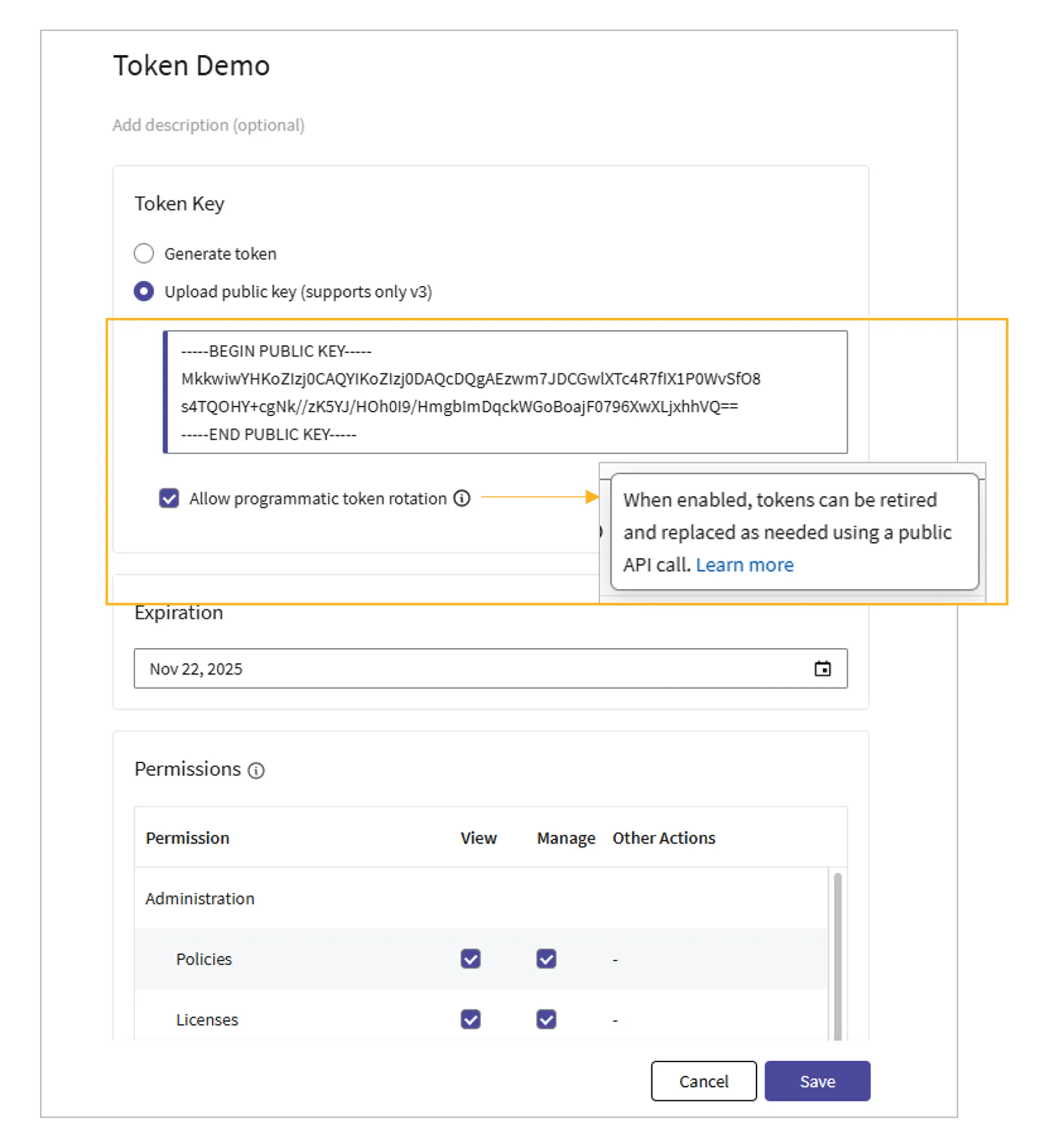
Enhanced Public API capabilities
- Create geofences via third-party tools to automate policies and integrate location-based triggers into your existing systems.
- Automatic token renewal at expiry for uninterrupted integrations and simplified API management.
Together, these upgrades make it easier than ever to embed Absolute Secure Endpoint into your broader IT and security ecosystem.
Action thresholds for greater control
Administrators can now set a maximum daily action limit per account, ensuring better workload balance and preventing automation overload in large environments.
Device Wipe optimization for faster data sanitization
Our Cryptographic Device Wipe capability now executes faster on encrypted devices by offering the option of skipping unnecessary erasure of unused space — accelerating secure decommissioning while maintaining compliance with NIST SP 800-88 and HIPAA standards.
Anti-malware scanning built into Application Resilience
When uploading installer files as part of Application Resilience policy configurations, files are now automatically scanned for potential malware — preventing threats before they reach endpoints and reinforcing your application self-healing workflows.
Rehydrate enhancements for smarter endpoint recovery
Absolute Rehydrate now offers expanded functionality and clearer operational visibility:
- Detects devices not eligible to run Rehydrate playbooks
- Provides improved tracking of execution status
- Displays passcodes used in “break-glass” recovery scenarios for audit and verification
These refinements make remote recovery more secure, transparent, and efficient — critical for reducing downtime during IT or security incidents.
What this means for your endpoints
The new Secure Endpoint 10.1 capabilities help unify IT and security operations under one resilient platform. With streamlined workflows and smarter automation, organizations can:
- Reduce administrative overhead while improving response times
- Integrate third-party tools more seamlessly via expanded APIs
- Execute secure device wipes faster to safeguard sensitive data
- Ensure safe, malware-free application deployments
- Restore compromised devices remotely with full audit visibility
It’s about turning operational efficiency into security strength — empowering endpoints to stay compliant, protected, and productive wherever they operate.
Availability & upgrade information
All enhancements are available now across the Absolute Secure Endpoint editions — Visibility, Control, Resilience, Resilience for Security, and Resilience for Automation.
Administrators can access the new features through their Secure Endpoint console. For managed customers, your Absolute representative or partner can assist with enablement and rollout.
Learn more
- Learn how Secure Endpoint helps secure endpoints through proactive and remedial measures.
- Read through the datasheets for Device Wipe, Application Resilience and Rehydrate to understand how the features help streamline IT and security operations.
- Request a demo to see how Absolute can simplify your endpoint operations.






