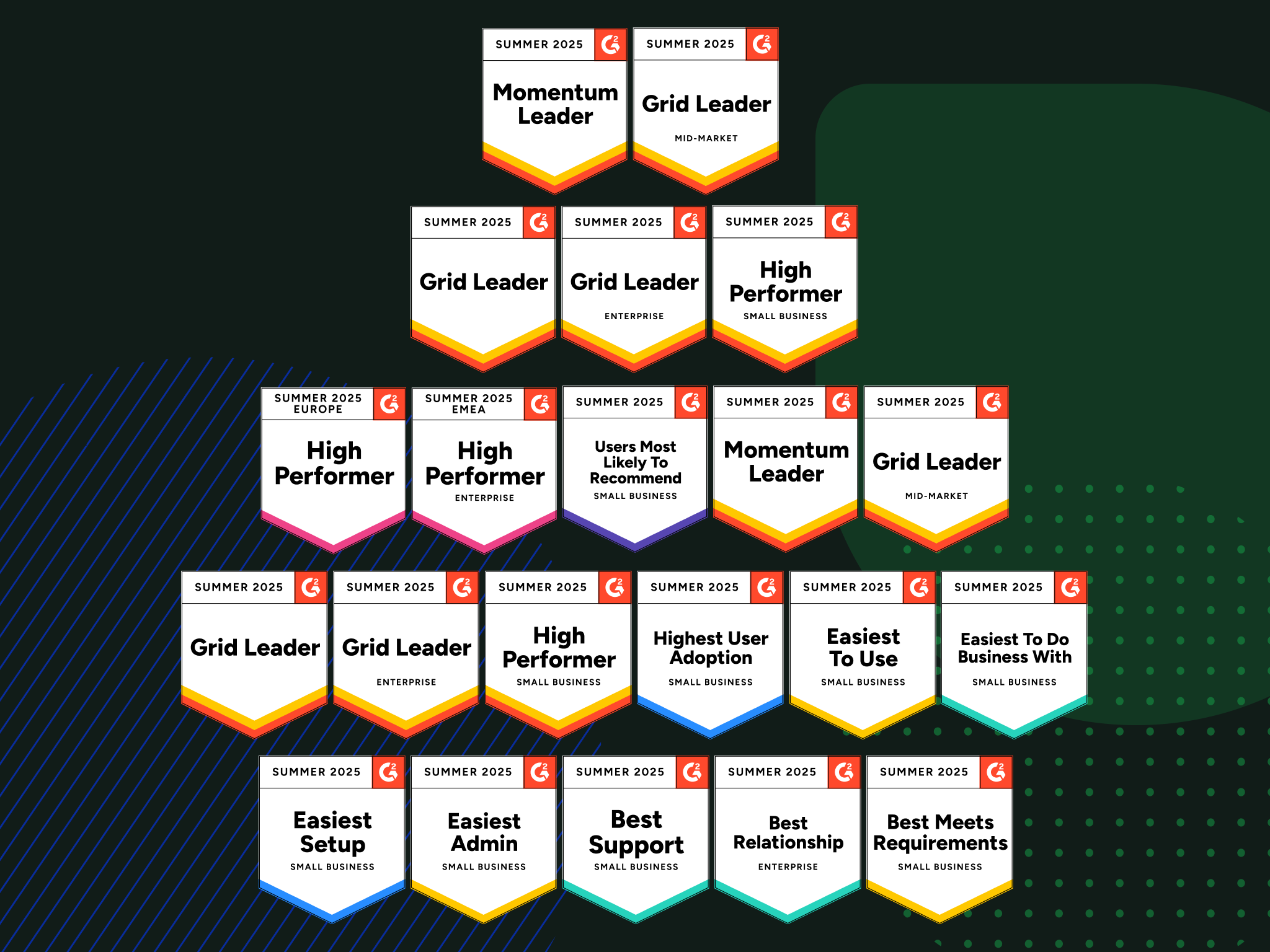
Absolute Named a Leader in G2 Summer 2025 Reports
A Trusted Benchmark for Buyers
G2 is the world’s leading business software review platform. G2’s seasonal reports are a trusted resource for IT and security professionals, offering unbiased insights based on verified customer reviews and market presence. Being named a leader represents exceptional performance in customer satisfaction and product capabilities.
For Summer 2025, Absolute Security—the only provider of self-healing, intelligent security solutions—leads across segments and regions, with recognitions including:

Absolute Security’s Leadership in Zero Trust Networking Software

Absolute Secure Access scored top marks thanks to its adaptive authentication, traffic monitoring, and seamless segmentation features—all verified by real user reviews.
Why Zero Trust Matters
Zero Trust Networking is a cornerstone of modern cybersecurity, ensuring that no user or device is trusted by default. G2 defines Zero Trust Networking software as a type of network security
and identity management solution used to implement the Zero Trust security model. Unlike the traditional network security systems, the Zero Trust model assumes every individual, both internal and external, is a potential threat until they are verified.
The Summer 2025 Grid® Report for Zero Trust Networking Software aims to help technology buyers choose the right partner for zero trust networking.
Absolute Secure Access helps leading organizations strike the balance between airtight security and operational agility:
- Adaptive Authentication: Dynamically verify every user and device, every time.
- Network Segmentation: Minimize exposure to breaches and robust policy enforcement to mitigate risks.
- Built-In Threat Detection: Spot and stop risks before they disrupt your systems.
When uninterrupted access is mission-critical, Absolute keeps remote and mobile users secure—ensuring continuity without compromise. Trusted by organizations like NHS Norfolk Community Trust for safeguarding sensitive data under pressure.
Absolute’s customers consistently highlight the platform’s ability to simplify Zero Trust implementation while enhancing security.
“Proven reliability and dependability – satisfied customer for over 10 years.”
My organization has been an Absolute Secure Access customer for over 10 years on approximately 30-40 mobile terminals in vehicles. It’s incredibly dependable and reliable. My team appreciates how easy it is to manage and configure. The best feature is it executes and connects before windows login and better emulates being ‘on the LAN’ better than any other VPN I know of.
VERIFIED USER IN GOVERNMENT ADMINISTRATION
MID-MARKET (51-1000 EMPLOYEES)
Absolute Security’s Leadership in Endpoint Management Software

More than just IT hygiene, our solutions help you build a resilient, secure foundation. Trusted by customers and recognized for leadership in endpoint security, Absolute Secure Endpoint scales protection across even the most distributed fleets.
The Importance of Endpoint Management
With hybrid workforces and increasing endpoint vulnerabilities, effective endpoint management is critical for maintaining security and productivity. G2 defines Endpoint Management software as products that help users keep track of devices in a system and ensure their software is secure and up to date.
The Summer 2025 Grid® Report for Endpoint Management Software is presented to help enterprise and education clients choose the right partner for endpoint management.
Absolute gives you the tools to secure every endpoint, ensure compliance, and respond to threats in real time.
- Real-time endpoint visibility and control: Monitor every device across your environment, on and off the network.
- Built-In Compliance: Automated patching and resilience against ransomware.
- Immediate Remediation: Detect and contain threats at the endpoint before they impact your system.
Absolute’s solutions are praised for their ability to reduce complexity while ensuring endpoint security and compliance.
“Absolute is a must for any IT department inside any organization.”
The solution works reports and helps to extend our frontline. Application resilience and device management are next level. The deployment to our fleet was hassle free and the tech team has been delightful to work with.
CRAIG J.
MID MARKET (51-1000 EMPLOYEES)
Extreme Resilience Isn’t a Strategy, It’s Imperative
Being named a leader in G2’s Summer 2025 Reports reflects our dedication to solving real-world challenges for IT and security teams.
Whether safeguarding a small, agile team or securing thousands of endpoints across global enterprises, our solutions prove that resilience is the foundation of operational success. Our leadership in "Results" within these categories underscores the critical role our technology plays in protecting organizations and enabling them to thrive.
As we continue to innovate, the focus remains on delivering resilient solutions that empower organizations to detect, respond to, and recover from threats. Explore our award-winning solutions and see why industry leaders trust us to secure their networks and endpoints, and stay tuned for the G2 Fall 2025 Report.