The Need for Enterprise Resilience
The nature of enterprise resilience is changing. For years, the focus has been on bouncing back after a disruptive event. But today, simply recovering is not enough. The new imperative is to emerge from incidents not just intact, but stronger, smarter, and more secure than before. This is the essence of anti-fragility, and it represents a fundamental shift in how we approach cybersecurity and business continuity.
Back in January, I shared how we're expanding and further unifying the Absolute Resilience Platform to address critical challenges and opportunities. As part of this evolution, we announced Absolute Rehydrate, available as a tech preview, a capability purpose-built to address the costly challenge of operational downtime. The feedback from our customers and partners is clear—the ability to remotely restore a device to a trusted state, even when its operating system is compromised, is a true game-changer.
Today, I am proud to introduce the availability of Absolute Rehydrate—the solution to recover devices automatically at scale—in minutes, not days—to stop downtime before it disrupts your business.
Absolute Rehydrate sets a new benchmark for proactive endpoint recovery—empowering organizations to stop downtime before it disrupts business. With this capability, IT and security teams take decisive control in moments that matter, transforming adversity into opportunities for deeper resilience and operational confidence.
The Tyranny of Downtime
Every IT and security leader knows the pain of a downed endpoint. Whether from a sophisticated ransomware attack or a critical system failure like a Blue Screen of Death (BSOD), the result is the same: a halt in productivity, a drain on IT resources, and a direct impact on the bottom line. The recovery process has traditionally been slow, manual, and expensive, often requiring devices to be shipped back to IT for manual reimaging. This process can take days or even weeks and that is simply unacceptable in today’s distributed workforce.
Events like the widespread IT outages seen in recent years demonstrate how quickly a localized issue can cascade into a global business catastrophe. The cost of downtime is measured not just in lost revenue, but in damaged customer trust and eroded operational confidence.
Absolute Rehydrate directly confronts this challenge. It gives IT and security teams the power to recover compromised devices in minutes, not days. With a single click, you can execute a remote restoration, by-passing a corrupted operating system to restore a device to a fully trusted and compliant state. This is made possible by our unique, undeletable connection embedded in the firmware of over 600 million devices. It is a last line of defense that you can always count on.
From Resilience to Anti-Fragility
Absolute Rehydrate is designed to stop downtime before it disrupts your business. It goes beyond simple recovery, empowering your teams to respond faster, reinforce your security, and keep operations moving—no matter the disruption. Absolute Security has a unique ability to operate below the OS, enabling remote recovery even when the system is bricked.
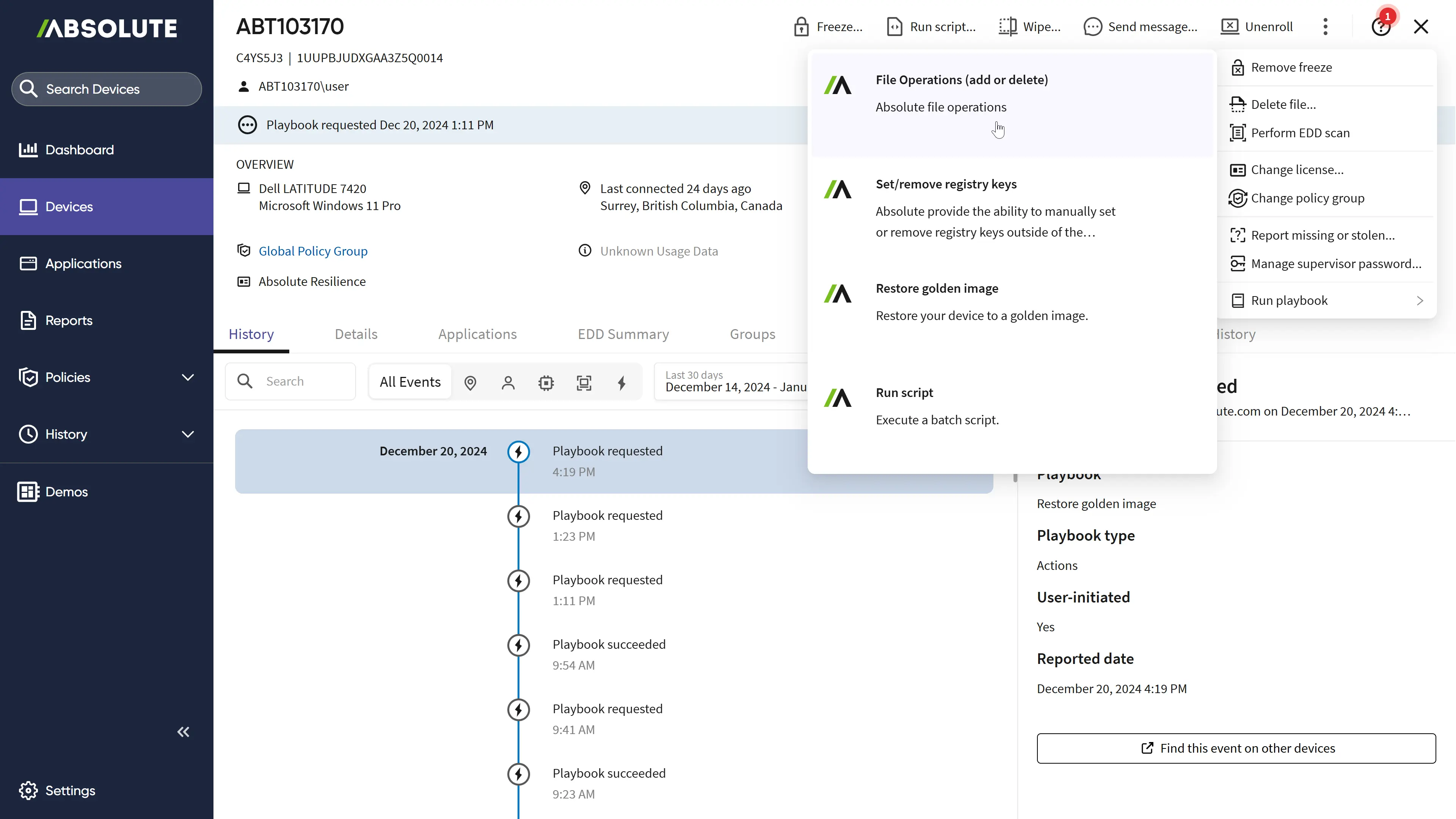
What does that mean in practice?
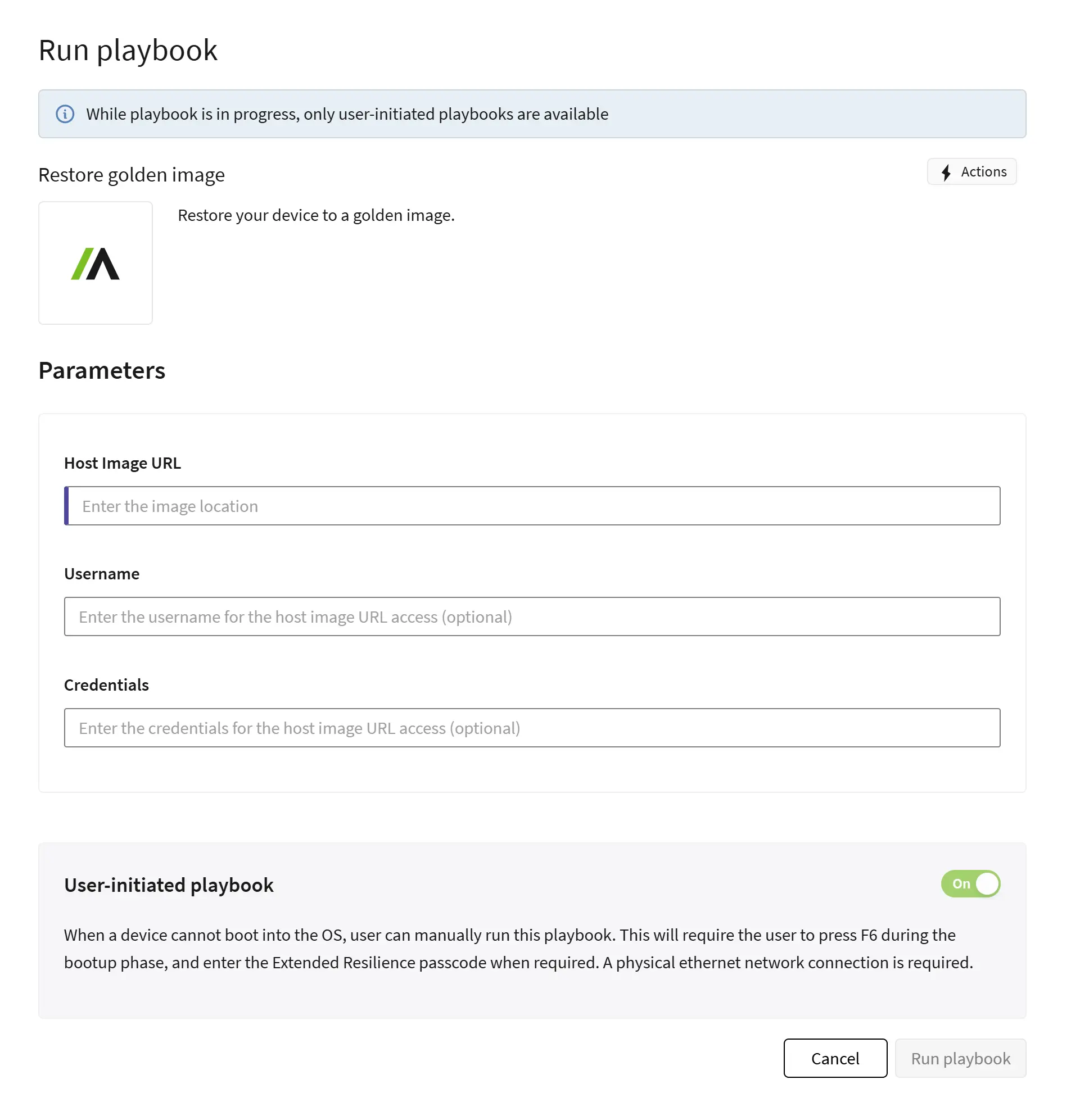
- Surgical and Scalable Remediation: Absolute Rehydrate enables precision recovery at scale. Beyond restoring a full golden image, you can deploy surgical playbooks to perform specific actions. This includes deleting malicious files, repairing registry keys, or executing custom scripts to restore and harden a device after an incident. You can execute these precise actions at scale across your entire fleet, whether devices are connected via wired or wireless networks.
- Automated and Configurable Control: Absolute Rehydrate includes new parameterized playbooks and API support. This allows you to integrate Rehydrate into your existing security ecosystem and automate complex recovery workflows. Instead of just reacting, you can build a system that automatically responds to threats and strengthens your defenses in real time.
- Turning Insight into Action: Each recovery event is a learning opportunity. By analyzing the incident and using Rehydrate to apply targeted fixes and remediations at the time of recovery, and Resilience for Automation to ensure they remain continuously in place post-recovery, you continuously improve your organization's resilience. You are not just resetting a device; you are reinforcing it against future attacks. This transforms your incident response from a reactive cleanup crew into a proactive engine for improvement.
Stopping Downtime: Beyond Endpoint Recovery: Absolute Rehydrate and the New Era of Anti-Fragility
Absolute Rehydrate sets the foundation for enterprise resilience, empowering organizations to maintain continuity and confidence by stopping downtime before it disrupts business. With a firmware-embedded, self-healing foundation, it provides the assurance organizations need to maintain business continuity—restoring endpoints in minutes and delivering proactive control where it matters most.
We are empowering organizations to move beyond the fear of downtime and embrace a new standard of operational readiness. When you can recover any endpoint, anywhere, in minutes, the entire dynamic of incident response changes. You can act with confidence, knowing you have uncompromised control over your devices when it matters most.
This is the future of enterprise resilience. We invite you to see it for yourself.
Explore how Absolute Rehydrate can transform your approach to business continuity
- See it in action with our interactive product tour
- Download the Rehydrate Data Sheet for features and benefits
- Calculate your potential savings with our online calculator
- Visit the Rehydrate page for more resources






