The shifting future of work
From improved productivity outputs to happier employees, the evidence is becoming clear: the future of work is hybrid work. The challenge today is most organizations still aren’t sure how to effectively execute on this new, preferred work style. Our new Endpoint Risk Report shows why addressing risk across any amount of remote work is a critical component to a successful formula, even as the details of a hybrid model are still being worked out.
Prior to the COVID-19 pandemic, most organizations required employees to spend the majority of their time on-site. The most common reason for this was an inability to support remote work. The global health crisis changed all that and today, a new McKinsey & Company hybrid work survey says most executives now expect the hybrid work model — where employees are on-site between 21 and 80 percent of the time, or one to four days per week — to increase.
Scores of other surveys confirm remote work delivers high productivity and continued customer satisfaction. Couple that with the majority of employees’ stated desire to continue working from home in some capacity (83 percent prefer it, says a new Accenture study) and there is little room for doubt the hybrid work model is here to stay, wherever it is possible.
The reality though is that while the shift to remote work may have felt sudden last year, the COVID-19 pandemic only accelerated what was already a natural progression toward hybrid work.
At its most basic level, hybrid work must include both a hybrid workforce and a hybrid technology environment that can support work from anywhere. Even pre-pandemic, most companies’ technology stack was increasingly shifting to include both a large number of cloud applications and longtail on-premises applications. IT has had to focus on supporting such a mix for some time now.
Endpoint risk in hybrid work
As we quickly pushed people out of offices and into homes with their devices in tow last year, we unfortunately lost visibility and control over their assigned devices and the data that resides on them. As a result, endpoint risk got riskier and failures to protect data got more expensive. According to the Cost of a Data Breach Report 2020 by the Ponemon Institute, the average cost of a breach ($3.86 million) was $137,000 higher for organizations with remote teams.
Absolute recently conducted the third annual Endpoint Risk Report based on an analysis of anonymized data from nearly 5 million Absolute-enabled devices across 13,000 customer organizations. In our research, we discovered four key trends impactful to maintaining device and data security in today’s hybrid work environment.
Known vulnerabilities remain unaddressed
In 2020, there was an increase in Windows 10 adoption with the most OS upgrade progress made in the Professional Services industry. While this is good news, it’s important to note that over 40 percent of the Windows 10 devices analyzed (across all industries) still run version 1909. This Windows 10 version was first released in 2019 and reached end of servicing in May 2021. Today, it is associated with over 1,000 known vulnerabilities.

The Endpoint Risk report also found the average enterprise Windows 10 device is 80 days behind in applying the latest available OS patches – of particular concern when you consider the volume of known vulnerabilities out in the wild. One piece of good news however is this patching lag is an improvement over the average of 95 days recorded just one year earlier. Companies have stepped up their vulnerability management programs in the last year, but more progress is needed if hybrid work is to be truly successful.
Data at-risk is skyrocketing
As more workers now operate off-network with growing regularity, it’s only natural to assume more data would be stored on their local machines. This assumption was confirmed in our study as 73 percent of all analyzed devices now contain sensitive data. The volume of at-risk data also grew at an alarming rate, including Personally Identifiable Information (PII) and Protected Health Information (PHI). This sensitive data carries the highest compliance failure fines as well as financial and reputational damage risk when breached.
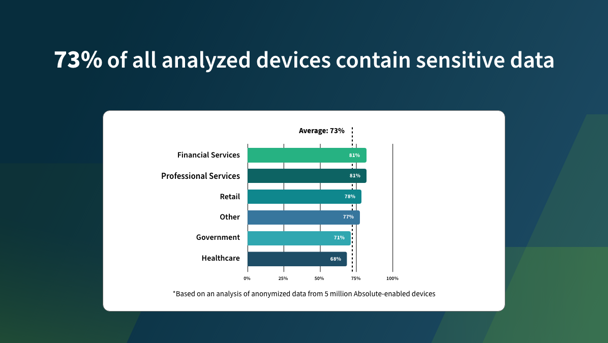
Compounding the risk of exposure, 23 percent of devices with high levels of sensitive data found on them also reported unhealthy encryption controls – a best practice security measure for protecting personal data and a solution that will satisfy compliance requirements. But only if it’s working as intended. Security controls, including encryption, regularly degrade and fail over time unless they are properly monitored and maintained.
Endpoint complexity is exacerbating risk
Remote work devices typically have more applications installed than those on a strictly in-office machine. More is necessary to support and secure work from home. In 2020, the average number of applications per device increased to 96, our Endpoint Risk report discovered. Out of those applications, 11.7 of them are security controls including encryption, anti-virus, and VPN. This figure is up 12 percent over last year.
This multitude of tools can cause over-burdened systems, colliding agents, and resultingly, impeded health. For this reason, complexity itself should be considered a notable security risk. When those applications are installed on off-network devices and therefore out of reach of IT’s standard updating services, this risk grows further.
Beyond knowing whether security tools are working as intended is determining ROI in all these tools. This too is a troublesome challenge for most organizations, particularly as scrutiny over budgets grows. We know from a separate study we commissioned with Forrester that just 38 percent of study respondents said they could measure the return on their company’s security investments. Lack of investment insight undermines the best efforts of too many security teams.
Compromised security controls are widening the attack surface
Left unchecked, every one of the 11.7 security controls on these devices can be considered a potential attack vector. Inevitably, their effectiveness measurably degrades over time and that creates risk. With remote work, this can happen because IT doesn’t have the ability to update security controls remotely, remote workers try to update their tools themselves unsuccessfully, and/or they disable or try to remove them entirely because they seemingly disrupt productivity.

Whatever the reason for failing security controls, our research found that 1 in 4 devices or 25 percent have unhealthy applications and this extends to critical applications. 34 percent have unhealthy anti-virus/anti-malware, 27 percent have unhealthy VPN, 23 percent have unhealthy encryption, and 19 percent have unhealthy client management. Each one of these unhealthy agents offer attackers yet another foothold into your systems and more chances to steal data and generally wreak havoc.
Gaining visibility and control
Effectively executing a hybrid work model requires much more than deciding who should be in the office when. Managing the risk that remote endpoints bring is a critically important piece of the hybrid work model puzzle and companies are pushing to put a plan in place. But notably, more than two-thirds of North American companies surveyed by IDC say they struggle to strike the right balance between flexibility and security for their hybrid work employees.
As we return to a world that includes business travel, in-person conferences, and workforces newly enabled to work from anywhere, knowing where not to compromise is critical. Cybercrime will go on and hackers will evolve their attack methods. In response, companies must take action to strategically measure the viability and effectiveness of their existing security controls. With the right level of visibility and control across all devices, it is possible to eliminate blind spots, identify weaknesses, and quickly mitigate threats.
Absolute fortifies endpoint environments with Endpoint Resilience™ or the ability for endpoints and critical security controls to autonomously maintain a secure operating state. The Absolute Platform enables a secure, unbreakable connection to every endpoint no matter where it is, delivering unmatched visibility and intelligence into devices, data, and applications across the environment.








