Absolute Security Blog
Get expert insights on endpoint resilience, Zero Trust, ransomware defense, digital transformation, and more—so you can stay ahead of what’s next.
Most Recent
Bolster Your IT and Security Resilience with Absolute Security’s Leadership Solutions
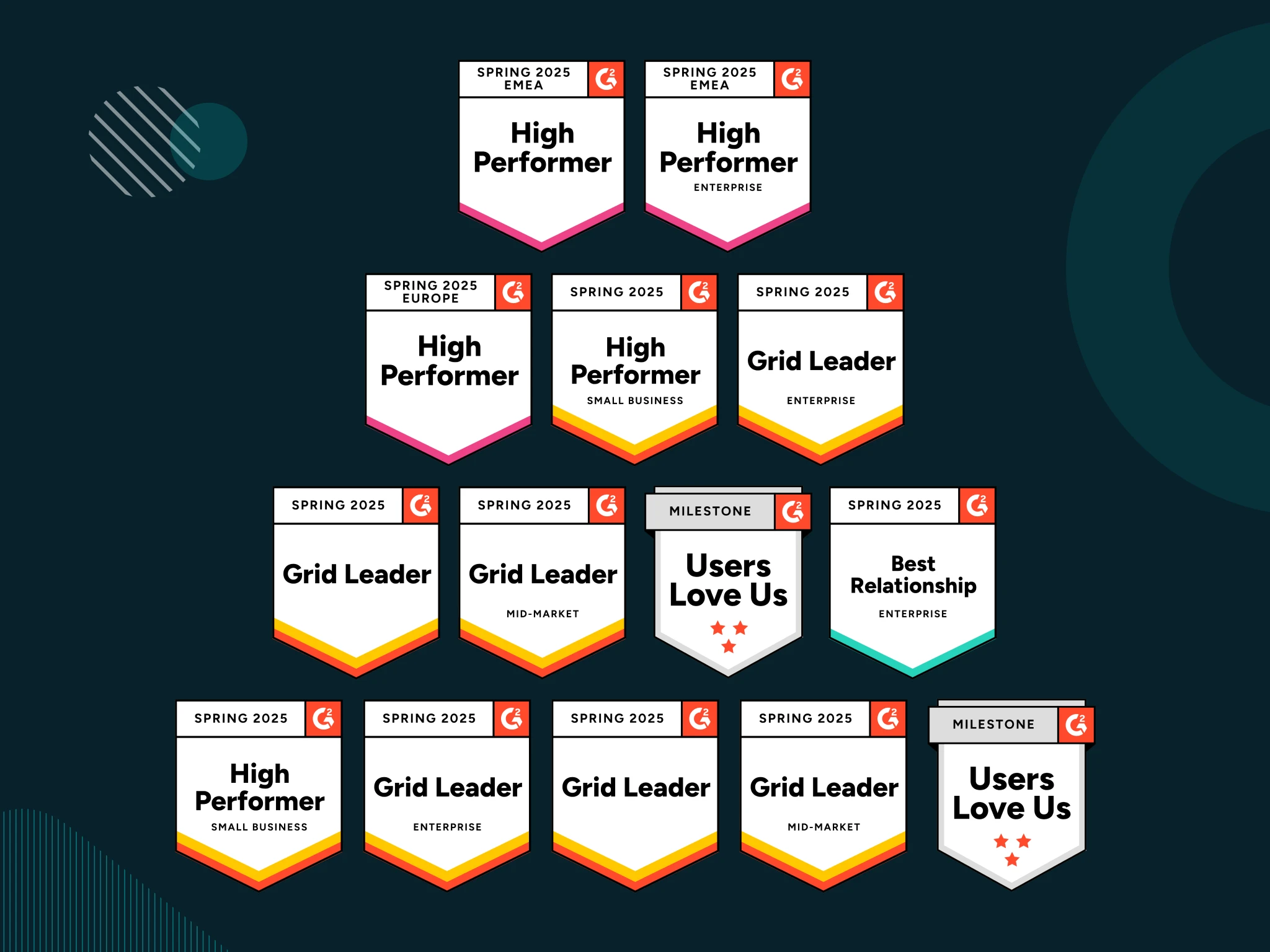
Bolster Your IT and Security Resilience with Absolute Security’s Leadership Solutions
May 28, 2025
Empowering MSPs to Boost Enterprise Resilience Across Environments

Empowering MSPs to Boost Enterprise Resilience Across Environments
May 23, 2025
Absolute Enhances Zero Trust with Secure Access App Connectors

Absolute Enhances Zero Trust with Secure Access App Connectors
April 22, 2025
Microsoft Patch Tuesday June 2025: Critical Fixes and Urgent Updates

Microsoft Patch Tuesday June 2025: Critical Fixes and Urgent Updates
Microsoft’s June Patch Tuesday delivers 66 security fixes, including 10 Critical and weaponized threats. Learn which systems are most at risk and how to patch fast.
June 11, 2025
Add title here

Add title here
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Et ille ridens: Video, inquit, quid agas; Cur, nisi quod turpis oratio est? Duo Reges: constructio interrete. Tu quidem reddes; Oratio me istius philosophi non offendit;
Add title here

Add title here
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Et ille ridens: Video, inquit, quid agas; Cur, nisi quod turpis oratio est? Duo Reges: constructio interrete. Tu quidem reddes; Oratio me istius philosophi non offendit;
Blog Library
Oops! Something went wrong while submitting the form.
No results found.
There are no results with this criteria. Try changing your search.

Expert Insights
Microsoft Patch Tuesday June 2025: Critical Fixes and Urgent Updates
Microsoft’s June Patch Tuesday delivers 66 security fixes, including 10 Critical and weaponized threats. Learn which systems are most at risk and how to patch fast.
June 11, 2025
Endpoint Resilience
Unified Endpoint Management
Vulnerability and Patch Management
Compliance

Products & Solutions
Bolster Your IT and Security Resilience with Absolute Security’s Leadership Solutions
In today’s unpredictable security landscape, resilience is key. See why Absolute Security’s G2 Spring 2025 recognition in Endpoint Management and Zero Trust Networking matters for organizations ready to adapt, respond, and thrive in the face of disruption.
May 28, 2025
Zero Trust
Endpoint Resilience
Access Resilience
Resilience
IT Asset Management

Products & Solutions
Empowering MSPs to Boost Enterprise Resilience Across Environments
Boost efficiency and endpoint security with Absolute Resilience for ConnectWise. Learn how MSPs can streamline operations and secure customer devices.
May 23, 2025
Endpoint Resilience
IT Asset Management
Ransomware

Products & Solutions
Absolute Enhances Zero Trust with Secure Access App Connectors
Enhancements to Secure Access for fast, end-to-end zero trust connectivity and security to public/private clouds and data centers.
April 22, 2025
Zero Trust
Application Resilience
Data Protection

Expert Insights
AI Moves Faster than Security, CISOs Say Resilience is Way Forward
With organizations embracing AI, Absolute Security’s newest survey of 500 U.S.-based CISOs revealed alarming and unexpected findings.
April 17, 2025
Resilience
Generative AI
Threat Protection

Expert Insights
Microsoft Patch Tuesday April 2025
Microsoft’s April Patch Tuesday: 120 Fixes, Including Critical and Weaponized Threats.
April 8, 2025
Compliance
Resilience
Application Resilience

Expert Insights
Microsoft Patch Tuesday March 2025
As always, Patch Tuesday brings critical updates and security fixes to keep your systems protected. Here’s a breakdown of the most significant issues and why you should prioritize addressing them immediately.
March 11, 2025
Compliance
Resilience
Application Resilience

Expert Insights
Microsoft Patch Tuesday February 2025: 53 Fixes, Including Weaponized Threats
After January’s record-breaking Patch Tuesday release, February’s update is significantly smaller, addressing 53 vulnerabilities. However, this month’s fixes include two actively exploited vulnerabilities and two publicly disclosed ones.
February 11, 2025
Compliance
Resilience
Application Resilience

Products & Solutions
Debunking Myths About Secure Access Solutions
We’d like to set the record straight with facts about the strengths of our solution and why we’re still the cornerstone technology and trusted choice for over 2,500 Public Safety and First Responder organizations worldwide for over two decades.
February 6, 2025
Generative AI
Threat Protection
Access Resilience
Resilience

Products & Solutions
Introducing New Resilience Capabilities to Strengthen Endpoint Cyber Resilience While Reducing Cost and Complexity
This blog post covers how the new Patch, Remediate, Automate and Rehydrate capabilities empower organizations to boost their cyber resilience through both proactive and remedial measure.
January 27, 2025
Endpoint Resilience
Resilience
Threat Protection
Application Resilience

Products & Solutions
Enhancing IT Efficiency and Cyber Resilience Through Automation
The Automated Actions capability empowers IT and Security teams to leverage automation as part of their IT and incident response practices to boost efficiency and cyber resilience.
November 20, 2024
Endpoint Resilience
Application Resilience
Compliance

Products & Solutions
Going Beyond Traditional SSE
Absolute Secure Access Enterprise offers resilient SSE, endpoint compliance, and secure access to private apps, websites, and cloud, from a single console.
November 12, 2024
Resilience
Ransomware
Data Protection
SASE and SSE

Expert Insights
How to Achieve Cyber Resilience
How to build a resilient infrastructure that defends against attacks, zero day threats, and ensures fast recovery.
October 30, 2024
Resilience
Endpoint Resilience
Compliance
Ransomware

Products & Solutions
Absolute Unwraps AI Threat Insights
Get proactive AI alerts on suspicious behavior — Comprehensive alerts on user, device, network, and application behavior to detect issues before they become problems.
September 19, 2024
Generative AI
Access Resilience
Threat Protection
Shadow IT
Ransomware

Inside Absolute
Absolute Security Acquires Syxsense: Making Cyber Resilience Accessible to the Global Enterprise
Absolute Security has acquired Syxsense, the automated endpoint and vulnerability management solution to extend cyber resilience to the global enterprise.
September 5, 2024
Endpoint Resilience
Resilience
Application Resilience
SASE and SSE

Products & Solutions
Absolute Security Automates Remediation for CrowdStrike and other Windows BSOD Incidents
On July 19, 2024, CrowdStrike’s update caused a BSOD outage. Absolute Security provided tools to remotely repair affected endpoints and prevent future issues.
July 30, 2024
Endpoint Resilience
Compliance
Resilience

Products & Solutions
Applied Resilience with Absolute Secure Endpoint
Align cyber resilience goals to real-world threats and implement a strategy to adapt to multiple failure points if endpoint defenses are impaired during an attack.
July 10, 2024
Endpoint Resilience
Threat Protection
Resilience

Expert Insights
Survey Says UK CISO's Top Threats are Ransomware and Mobile Work
Survey reveals UK CISOs’ concerns about poor cyber resilience, AI risks, and the growing threat of ransomware ahead of Infosecurity Europe 2024.
May 29, 2024
Endpoint Resilience
Resilience
Ransomware
Remote Work

Inside Absolute
Absolute Security the Leader in Cyber Resilience
Absolute Software is now Absolute Security, offering new solutions that provide unmatched resilience against today’s most complex cybersecurity threats.
April 17, 2024
Resilience
Endpoint Resilience
Zero Trust
Ransomware

Inside Absolute
Forrester Includes Absolute Software in Security Services Edge (SSE) Landscape Report
Forrester's 2024 report highlights Absolute’s leadership in SSE, helping enterprises achieve resilience with cybersecurity and risk-based compliance strategies.
February 21, 2024
Resilience
Access Resilience
Compliance
Sorry, no items found...