The Challenge of Securing Remote Devices and Endpoint Management
With work-from-home and hybrid work plans now here to stay, IT and security practitioners will have to adapt their endpoint management practices to effectively monitor and secure devices operating off the corporate network for the foreseeable future. This remote environment presents unique challenges in ensuring devices have up-to-date applications, patches, and security controls in place while balancing end user impact to ensure productivity is never disrupted. Furthermore, with the recent uptick of ransomware and other cyber-attacks, the implementation of pro-active and robust security policies to safeguard devices and data must now be part of every organization’s internal processes.
You can’t secure what you can’t see, however. The foundation behind executing an effective endpoint security strategy is having unparalleled visibility into your endpoint environment. As no organization is the same, IT and security administrators require the means to collect custom device data points that are important to their organization’s needs. Often, these data points are not easily accessible through the standard device and security management tools available at their disposal. SaaS based product offerings today lack the capability for users to customize device data points they collect across their endpoints.
Unlocking Custom Data Points with the Absolute DataExplorer™
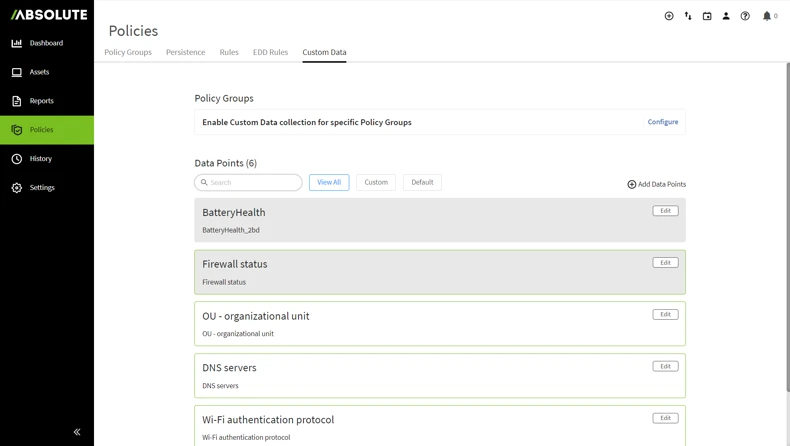
In response to these requirements, Absolute recently announced enhanced endpoint data collection capabilities that enable customers to capture custom device data points uniquely important to their internal organization policies. Specifically, the new Absolute DataExplorer feature can be leveraged to customize the collection of data points through a Windows Management Instrumentation (WMI) query or as a value in the Windows registry. Examples of potential data points that can be captured to assist with specific IT or security tasks include:
- Access granular Windows registry entries to appropriately inventory devices.
- Identify potentially unauthorized applications or browser extensions.
- Verify network security parameters such as the local firewall status, DNS settings, and Wi-Fi authentication protocol.
- Monitor hardware component details such as battery and memory card information to identify devices that need to be retired.
- Confirm if a specific Windows service, process, or file is running on the device.
Absolute Resilience® customers can leverage the Absolute DataExplorer Builder, a block-based rule editor application that enables their IT or security teams to graphically define and configure their own data points, using logic expressions representing underlying JSON code.
Absolute Visibility® and Absolute Control® customers have access to the Absolute DataExplorer Library where they can choose from a growing list of Absolute-defined custom data points that can be activated directly through the Absolute Console.

Once a data point is configured and activated, it can be added as custom columns to any Absolute Console report to be monitored daily. This enhanced customization and granular visibility into their endpoint environment allows organizations to align their internal device management and security policies with specific business, operational, and regulatory requirements.

Closing Thoughts
As remote work continues to shape the modern business landscape, securing endpoints requires more than just standard solutions. The need for unparalleled visibility into endpoints is critical in ensuring that devices are fully protected, up to date, and compliant with internal and regulatory security policies.
With enhanced endpoint data collection, Absolute provides organizations the flexibility to tailor their security strategies to meet specific operational needs, ultimately safeguarding the entire digital infrastructure.
With tools like Absolute DataExplorer™ and the Absolute DataExplorer Builder, security teams now have the power to customize and fine-tune the data they collect, ensuring that they can monitor exactly what matters to their organization. Whether it’s detecting unauthorized apps, verifying network parameters, or monitoring hardware components, these capabilities bring a new level of control and transparency to endpoint management.
By incorporating these tools into their security strategy, organizations are better equipped to navigate the complexities of modern work environments. Moreover, this granular visibility supports proactive decision-making and faster responses to potential threats, which is crucial for maintaining a secure and resilient enterprise in the long run.
As businesses continue to adapt to the demands of a hybrid workforce, aligning security policies with customized endpoint data collection will be essential for maintaining business continuity and protecting sensitive data. Organizations looking to future-proof their security infrastructure should embrace solutions that allow for greater flexibility and control over their endpoint
Find Out More
Explore how Absolute can help you enhance your endpoint visibility and security with advanced data collection capabilities tailored to your organization's requirements.
Stay Connected
Want to stay connected? You’ve got options. Explore our resource library, follow us on LinkedIn, or book a demo to see our solutions in action.
About Absolute
Simply put: we’re undeletable. Embedded in more than 600 million devices, our cyber resilience platform delivers endpoint-to-network access security coverage, ensures automated security compliance, and enables operational continuity. Nearly 21,000 global customers rely on Absolute to protect critical assets and keep security applications running smoothly. Building lasting cyber resilience is our promise — are you ready?








