From IT Failure to Ransomware: Downtime Costs Millions



The problem
When an incident hits, the clock isn’t just ticking—your business is bleeding. Lateral movement accelerates, systems freeze, customers are impacted, and every minute of outage compounds financial & operational damage.
Most organizations rely on manual recovery steps. This leaves teams blind, controls offline, and operations at a standstill. Downtime doesn’t wait. Recovery shouldn’t either.
Rapid endpoint recovery matters
The numbers don't lie—and they’re getting worse. When incidents strike, the losses are immediate—and staggering. The following stats reveal just how high the stakes are.
Your disaster recovery strategy means nothing, unless you can control endpoint recovery securely. The alternative is a painstaking slog to manually restore each device individually, to ensure it doesn’t bring the whole network down again
Cybercrime and software failures cause disruptions that cost organizations more than a trillion dollars in losses annually.
How Absolute Security restores business continuity in minutes
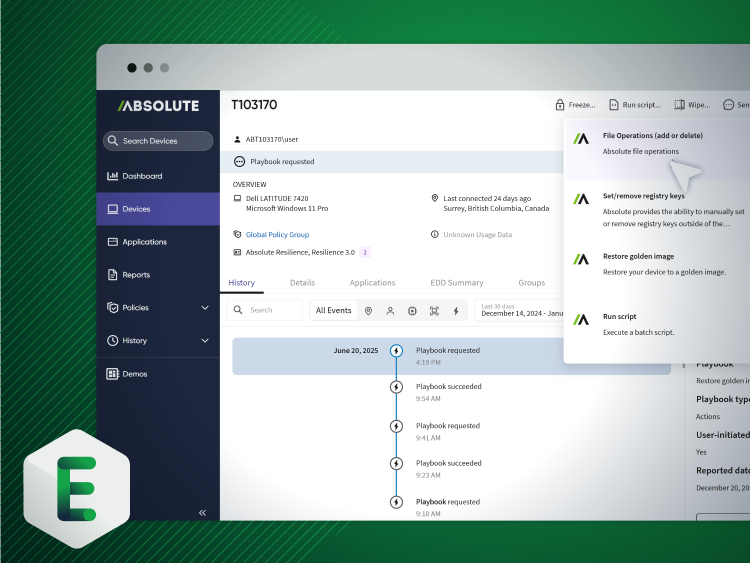
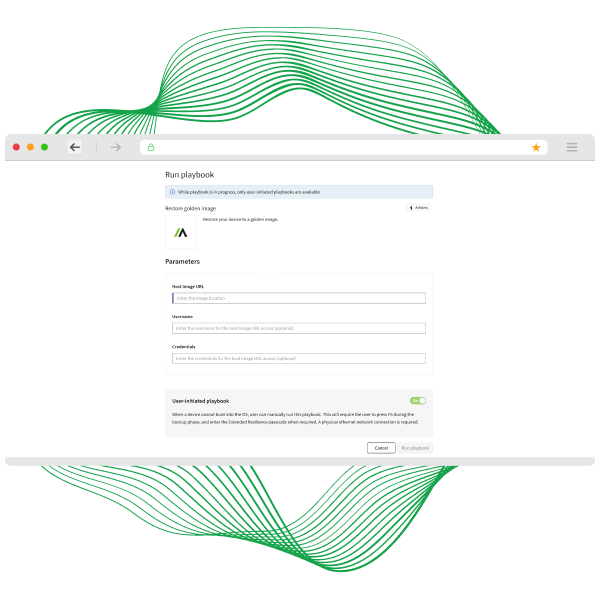
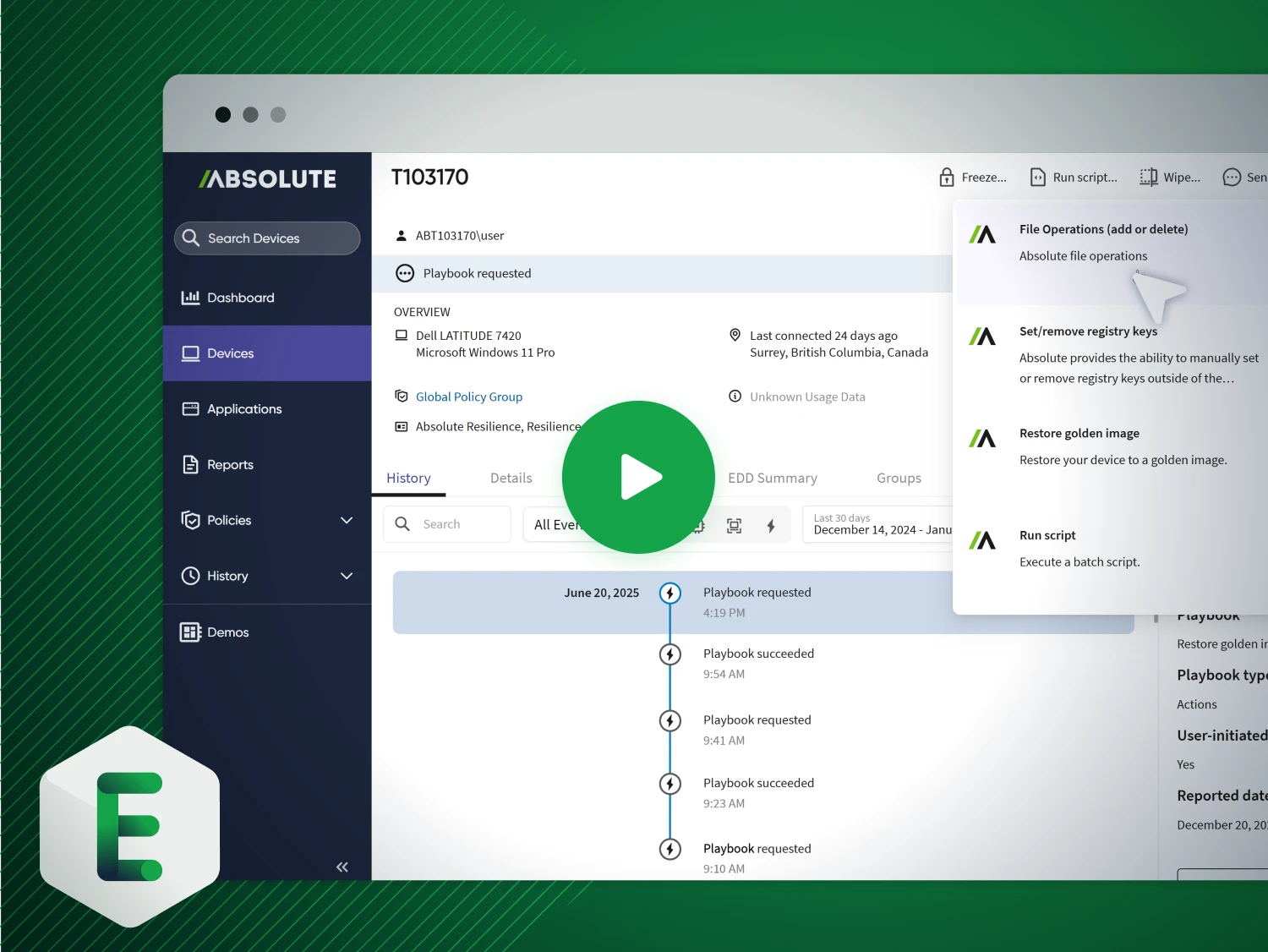
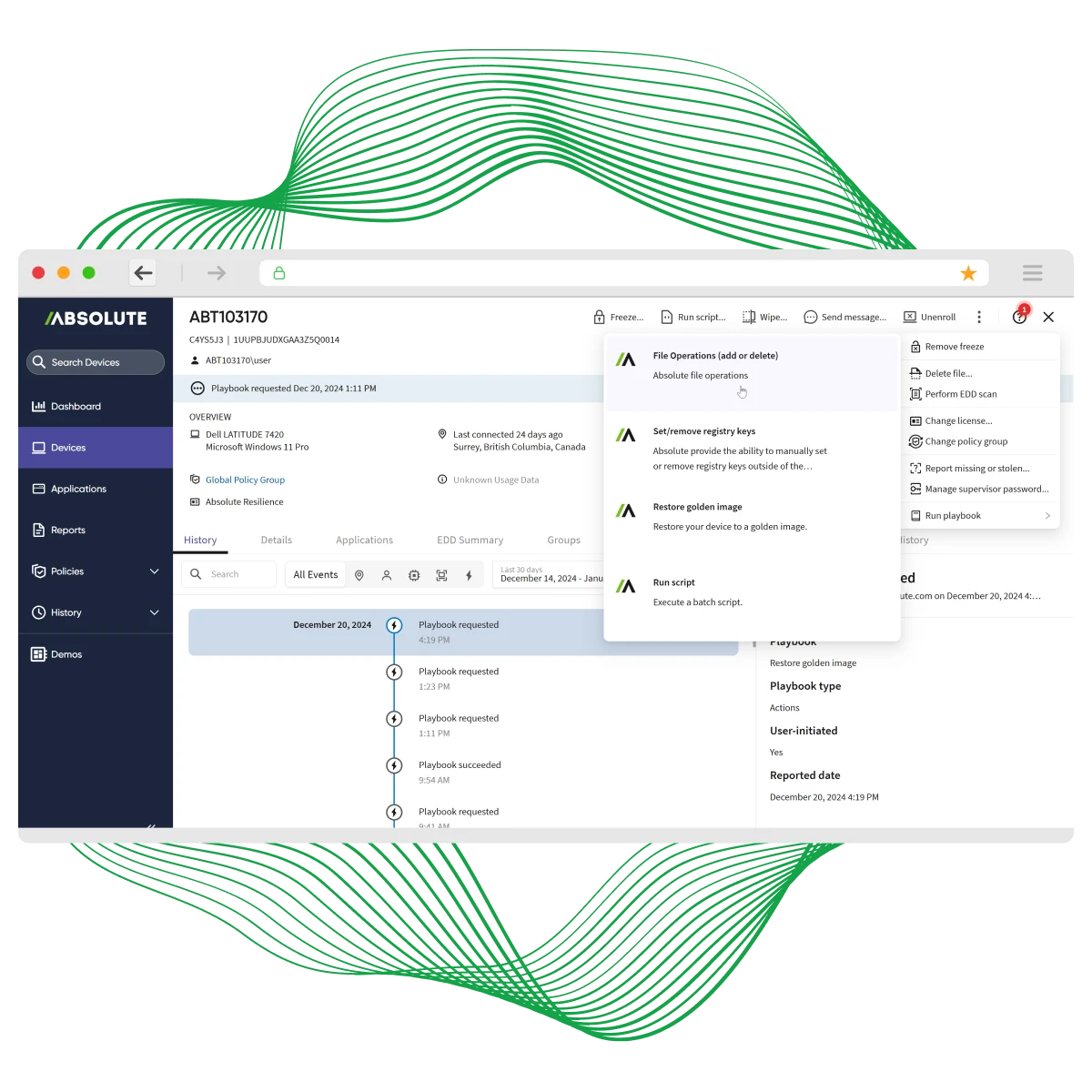
Absolute’s undeletable, self-healing connection—embedded in device firmware—guarantees access to every endpoint, even if it’s off-network, corrupted, or compromised. From anywhere, with a single click, you can isolate, freeze, or wipe compromised devices remotely. Trigger Absolute Rehydrate to restore a clean, trusted OS image and bring back operating systems, apps, and required controls with surgical precision—in minutes, not weeks. No desk visits. No shipping. No guessing.
See Rehydrate in action
Stop letting incidents dictate downtime. Absolute Rehydrate restores compromised devices to a trusted, compliant state—fast enough to keep your business running without disruption.
- Rapid Recovery: Bring back OS, apps, and security controls in minutes—not hours or weeks—no desk visits, no shipping.
- Precision Restoration: Trigger a clean, verified OS image remotely for full compliance and operational continuity.


Umm Al-Qura University: cyber resilience and rapid recovery at scale
Managing thousands of endpoints across a sprawling campus, Umm Al-Qura University needed real-time visibility, control, and compliance—plus the ability to recover compromised devices fast. With Absolute Secure Endpoint, they strengthened security, streamlined IT operations, and gained the power to rehydrate endpoints remotely and at scale.
- Persistent Visibility & Control: Track device status, monitor software, and enforce security policies across thousands of endpoints.
- Rapid, Remote Recovery: Restore OS, apps, and security controls with Absolute Rehydrate—minimizing downtime and eliminating costly desk visits or shipping.
Key capabilities for remote recovery

Rapid endpoint restoration to a trusted state

Remote containment: wipe, lock, or network‑isolate compromised devices

Rollback failed patches and undo misconfigurations fast

Forensic data collection without interruption

Session termination & access revocation to enforce Zero Trust

Firmware‑embedded persistence for always‑on recovery—even during attacks
Fall in love with Rehydrate
Absolute doesn’t just recover endpoints—we rehydrate them, all before the OS even boots. Our firmware-embedded, tamper-proof agent makes recovery fast, secure, and cost-effective.
- Restore & Remediate: Instantly bring back a trusted image, apply fixes, and patch faulty software at scale.
- Cut Recovery Costs: See how Rehydrate reduces downtime and lowers recovery expenses by up to 80% in our whitepaper.

Experience resilient recovery firsthand
See the power of Absolute Rehydrate—built into the firmware of 600 million devices—for seamless setup and instant remote recovery at scale.
- Rehydrate with One Click: Restore your own devices, test custom playbooks, and access the full resilience platform.
- Prove Business Continuity: Evaluate impact on operations and define your POV goals with real-world recovery scenarios.
Featured resources for Accelerate Incident Response & Endpoint Recovery
Incident response & endpoint recovery FAQ
Recovery is accelerated by fundamentally changing the equation. Instead of just reacting, this solution provides a persistent, self-healing connection to every endpoint. This enables critical actions in minutes, not months—roll back failed patches, restore ransomware-infected devices, or remotely wipe lost endpoints to prevent data breaches.
Traditional tools often fail when agents are disabled or lose connection—leaving businesses blind in a crisis. This platform ensures continuous, undeletable connectivity, always guaranteeing access and control. It’s about certainty and resilience when it matters most. It’s supported across a wide range of Windows PCs which is particularly important for enterprise organizations with mixed platform device environments. Plus, Rehydrate offers the option for undergoing a full reimage of Windows or more surgical actions such as adding or removing files, modifying registry or executing scripts, all from below the operation system layer.
Deployment is rapid, thanks to firmware-embedded technology present in most enterprise devices. No complex infrastructure required. Organizations typically go live and realize value across the fleet in days—not months—driving faster results and resilience.
Absolute serves enterprises, government agencies, and educational institutions that require persistent endpoint security, compliance enforcement, and real-time risk mitigation.
Yes. Built for global scale, the platform supports fleets of thousands to hundreds of thousands of devices without performance loss. Real-time visibility and control extend across the entire organization, regardless of size or geography.
