Stop Flying Blind with Your Inventory Management



The problem
How much of IT is just managing a carefully constructed illusion? We deploy agents to get a picture of our device fleet, but that picture starts decaying the second it's created.
Your CMDB, meant to be your source of truth, is likely riddled with stale data. This isn't just an inconvenience; it's a critical failure in endpoint asset visibility that leaves you flying blind.
The cost of guesswork
A compromised inventory creates a ripple effect of risk and waste. Every unseen device is a potential compliance violation. Every unmonitored endpoint is an open door for threats—from malware to unauthorized GenAl apps exposing company data.
Meanwhile, you're paying for software licenses on devices gathering dust. Without accurate IT asset tracking, your security is based on hope. It's a professional defense mechanism, but it's time to build a new moat. So, what's the solution?
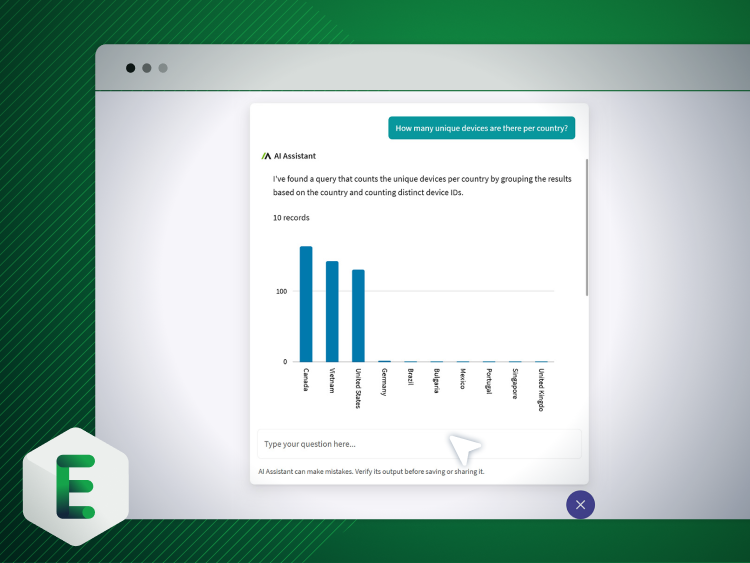
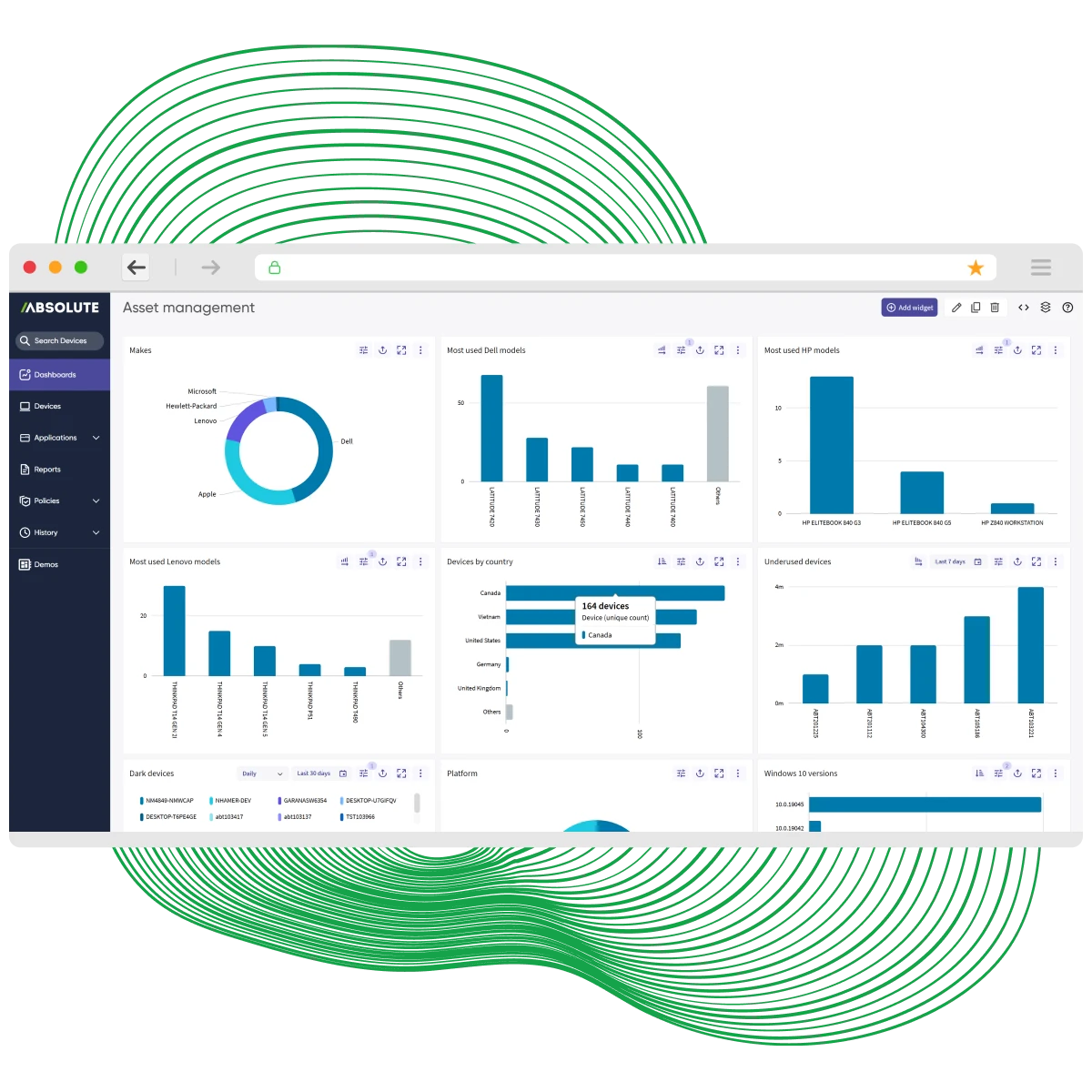
Absolute provides real-time data on our device fleet. 95% of returned devices are used, which means we get a second and third life usage on a device through our device reuse program, which is great for our sustainability efforts.
Visibility you can trust
The Solution: Visibility You Can TrustLet's stop pretending that fragile software agents give us the full picture.They don't. You need visibility you can trust, not just hope for. Absolute anchors your inventory in the one place that cannot be deleted, disabled, or fooled: the firmware.
This undeletable, self-healing tether creates a permanent line of sight to every device, on or off your network. It's the difference between chasing ghosts and managing facts. Finally, you can treat your CMDB as a source of truth, not a graveyard of stale data.
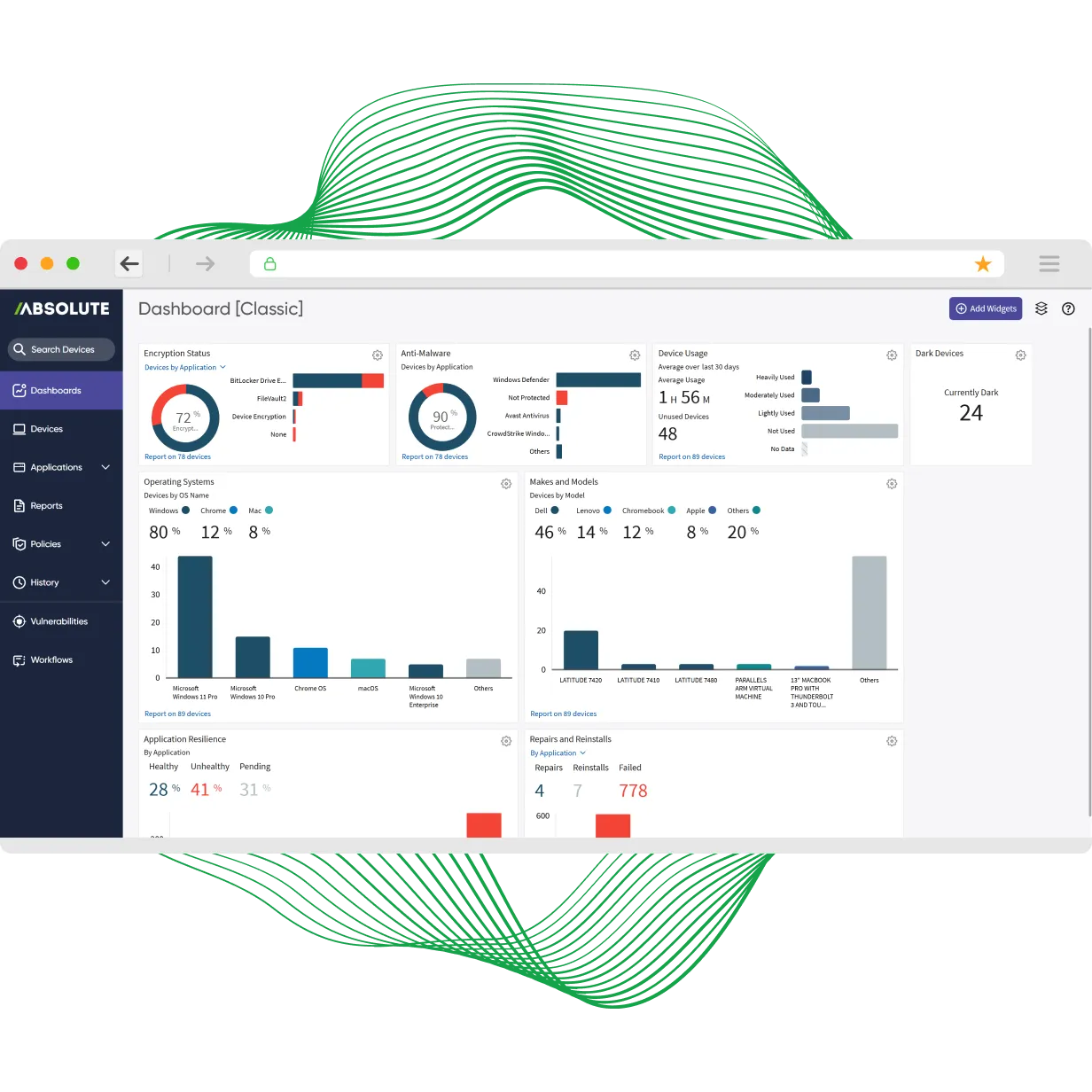
Stop managing illusions. See your entire fleet with absolute clarity.
Stop wasting hours manually tracking devices. Our AI-powered Asset Inventory Management gives you instant visibility, automated updates, and intelligent insights
- Predict issues before they happen
- Stay audit-ready without lifting a finger
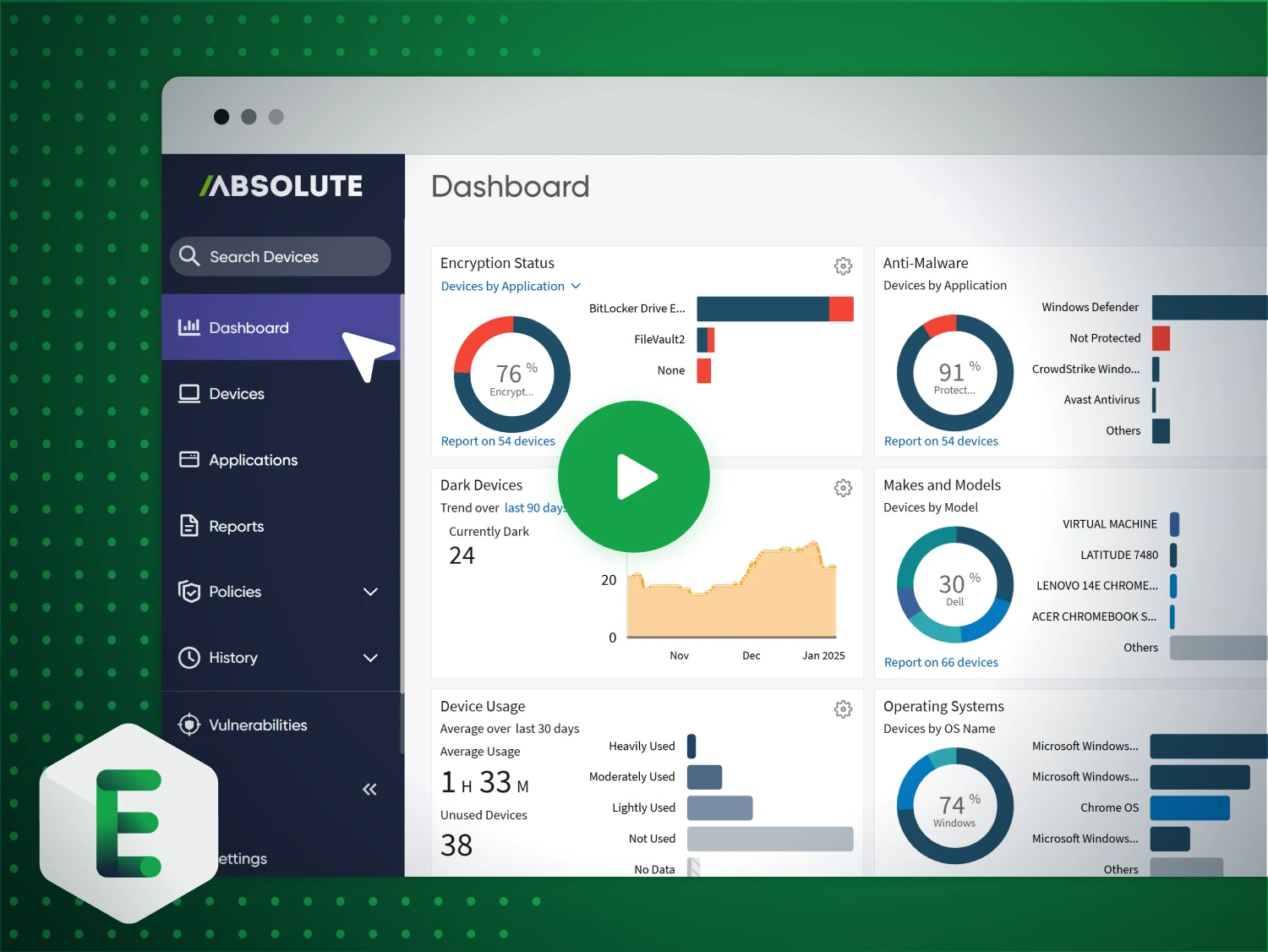


Endpoint visibility guaranteed
Tietoevry, a global IT services leader, needed complete visibility and control across a sprawling device landscape. With Absolute, they achieved real-time asset intelligence and automated compliance; without adding complexity.
- Full Endpoint Visibility: A single source of ruth for every device, app, and user, no matter where they are.
- Continuous Compliance & Control: Automated inventory accuracy and enforced security policies 100k+ endpoints.
Key capabilities for reliable asset inventory management
Your tools aren't looking deep enough
Most inventory solutions stop at the surface, leaving blind spots that attackers exploit. Our report reveals how firmware-embedded visibility closes these gaps, strengthens compliance, and ensures every device is truly visible and truly secure
Inside you'll learn:
- Why traditional tools fail without a firmware presence
- How deep visibility prevents hidden exploits
- Steps to achieve full-stack asset control
- Compliance without complexity

Request a trial
Forget hope-based IT. With Absolute, get undeletable, persistent visibility and control embedded at the firmware level. See how a free trial delivers certainty—automating device lifecycle tasks for real, measurable outcomes and experience control that's a physical fact
- Persistent, real-time device visibility and control—anywhere.
- Autonized lifecycle management for assets, patching, and secure disposal
Featured resources for IT asset inventory management
Asset inventory management FAQ
That’s a common frustration with traditional device inventory management. Many IT leaders grapple with hardware/software inventory tools reliant on software agents that can be removed or simply fail when a device is off the network. The accurate picture of endpoint asset visibility starts decaying the moment it’s created. Absolute stands apart through its connection embedded in device firmware, forming an undeletable, self-healing tether. This permanent link ensures continuous, real-time device inventory management and reliable CMDB accuracy. With trusted visibility to every endpoint, the CMDB evolves from a static record to a living inventory you can rely on.
This is a key question for effective IT asset tracking. Absolute isn’t just another layer to manage; it's the backbone that reinforces existing management, security, and hardware/software inventory tools. By anchoring its persistent connection in firmware, Absolute ensures that essential agents—UEM, EDR, and others—are present and functioning. Even on off-network devices, this platform validates your stack’s health and boosts endpoint asset visibility, making your entire security infrastructure more resilient and reliable.
Precision in endpoint asset visibility provides benefits far beyond a simple device count. For starters, superior device inventory management directly controls licensing costs; software licenses for “ghost” devices become a thing of the past, and hardware/software inventory can be right-sized to match actual business needs. Moreover, risk and compliance are transformed. Each unmanaged device is a compliance risk and a security gap. With IT asset tracking that offers complete visibility, proving compliance and ensuring every device is patched and protected becomes routine. The platform also reveals unsanctioned apps—including shadow GenAI tools—protecting sensitive data. Ultimately, accurate device inventory management strengthens financial health, compliance standing, and overall security posture.
The trial grants full access to Secure Endpoint, enabling end-to-end evaluation of device inventory management, endpoint asset visibility, and CMDB accuracy. With technology already embedded in the firmware of most enterprise hardware, activation is quick and seamless—no convoluted or multi-stage deployments required. Immediately during the trial, watch devices check in, including those previously unreachable. Test critical features like real-time hardware/software inventory, device location tracking, and the enrichment of your existing IT asset tracking and security systems. Experience first-hand the impact of visibility you can trust—without commitment.
Absolutely. This is about automating the aspects of device inventory management that typically drain IT teams—hunting for devices during audits, manual license reconciliation, or tracking hardware for refresh cycles. With automated fleet discovery, accurate hardware/software inventory, and real-time data feeding into your CMDB, teams eliminate repetitive investigative work. Audit-ready reports and automated syncing free up resources, allowing staff to focus on strategic initiatives. The result: endpoint asset visibility and IT asset tracking that delivers productivity, reduces manual effort, and empowers high-value work.
