Absolute for Healthcare
Delivering resilient and reliable endpoints and access for the healthcare industry

Minimize data leaks and strengthen compliance posture
Healthcare organizations need to manage vast quantities of highly sensitive data, while satisfying a complicated series of compliance regulations - e.g., HIPAA, HITECH, PCI DSS. Adding to this challenge, the digitalization of the healthcare industry has led to a highly distributed workforce that relies on secure network connectivity to do their jobs.
Focused on what matters to you
We are committed to providing solutions that meet the unique and evolving needs of healthcare organizations

Control costs of devices, apps, and mobile services

Establish cyber hygiene based on HIPAA, HITECH, PCI DSS

Minimize leaks of patient data

Respond to threats immediately

Optimized connectivity for tele-health staff

Reduced time to resolution for all connected workers
Strengthening Security and Compliance Posture through Cyber Resilience in Healthcare

Absolute’s latest research report demonstrates the importance of cyber resilience to strengthen your security and HIPAA/HITECH compliance posture.
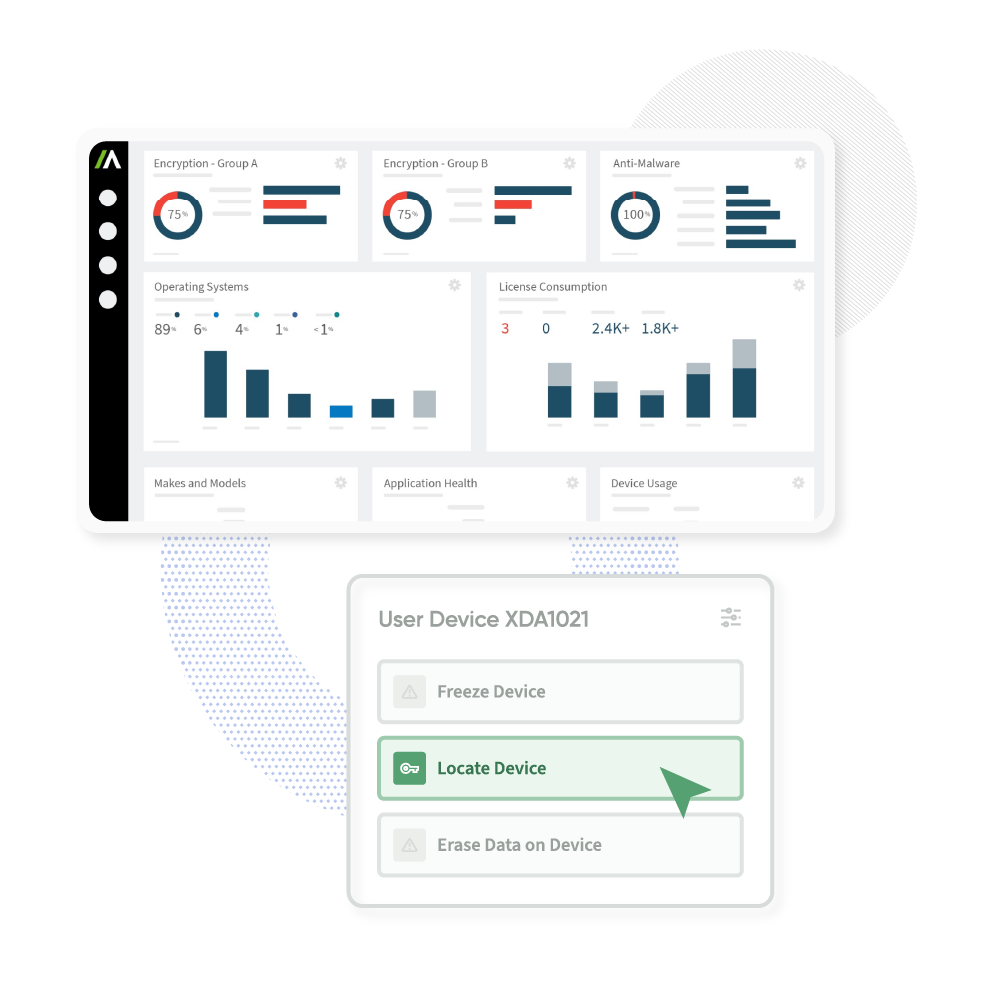
Reliable, resilient endpoints
Retain command of all your endpoints, all the time
- Boost your endpoint visibility – on or off your corporate network. Collect hundreds of data points about your devices’ location, security posture, and hardware/software inventory.
-
Take advantage of critical control functions such as remote file deletion and data wipe, freezing devices when at-risk, end user messaging, and establishing geo-fences.
-
Leverage critical resilience functions to secure endpoints from threats, respond to security breaches, and enable application resilience to automatically self-heal applications.

Reliable, resilient access
Ensure secure and optimized network access
- Leverage a secure, optimized tunnel built from the ground up for your workforce’s mobility and the modern edge
- Deliver the best user experience for the software-defined perimeter
- Leverage the best diagnostics and remediation for digital employee experience monitoring
What our customers love about Absolute
“Absolute Persistence gives us assurance that stolen devices don’t become breach liabilities. Our other tools were not able to detect these devices and give us the sense of security that we now have."
InfoSec leader, Healthcare

Featured Resources
Like what you're hearing?
See how Absolute can help your organization keep devices and sensitive healthcare data safe and secure.
Looking for more information? Join a product overview webinar
Not ready for a demo? Have some questions?





